
French government abandons Zoom and Microsoft Teams over security concerns
France intends to phase out non-European videoconferencing platforms such as Zoom and Microsoft Teams from its public administration, opting instead for a nationally developed …
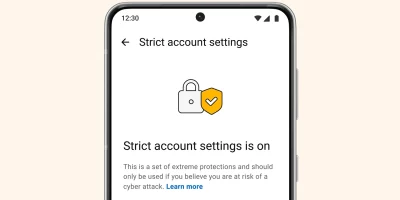
WhatsApp rolls out new security feature to protect users from sophisticated attacks
To add an extra layer of protection to its end-to-end encryption, WhatsApp has begun rolling out a new privacy and security feature called Strict Account Settings. It is …
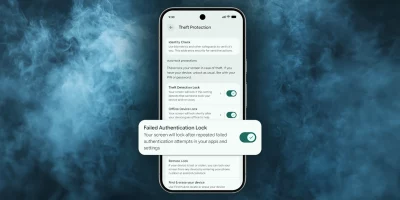
Android just got smarter at stopping snatch-and-run phone thefts
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use. These updates are available on Android …
CERT UEFI Parser: Open-source tool exposes UEFI architecture to uncover vulnerabilities
CERT UEFI Parser, a new open-source security analysis tool from the CERT Coordination Center has been released to help researchers and defenders examine the structure of …

Why prevention-first secrets security will define enterprise scale: Learnings from a leading telecom
Once a secret enters Git, it’s expensive to remediate. But the real problem runs deeper than cost. Grégory Maitrallain, Solution Architect at Orange Business, discovered …

Grammarly and QuillBot are among widely used Chrome extensions facing serious privacy questions
A new study shows that some of the most widely used AI-powered browser extensions are a privacy risk. They collect lots of data and require a high level of browser access. The …

Audits for AI systems that keep changing
Security and risk teams often rely on documentation and audit artifacts that reflect how an AI system worked months ago. ETSI’s continuous auditing based conformity assessment …

Fortinet starts patching exploited FortiCloud SSO zero-day (CVE-2026-24858)
Fortinet has begun releasing FortiOS versions that fix CVE-2026-24858, a critical zero-day vulnerability that allowed attackers to log into targeted organizations’ …

Attackers use Windows App-V scripts to slip infostealer past enterprise defenses
A malware delivery campaign detailed by Blackpoint researchers employs an impressive array of tricks to deliver an infostealer to employees without triggering enterprise …

Microsoft brings AI-powered investigations to security teams
Microsoft Purview Data Security Investigations is now available. The tool is part of Microsoft Purview and is intended for scenarios such as data breach and leak …

AWS adds IPv6 support to IAM Identity Center through dual-stack endpoints
Amazon Web Services has added IPv6 support to IAM Identity Center through new dual-stack endpoints. The update allows identity services to operate over IPv6 networks while …

Microsoft reveals actively exploited Office zero-day, provides emergency fix (CVE-2026-21509)
Microsoft released emergency Office security updates to fix a security feature bypass vulnerability (CVE-2026-21509) that its threat intelligence and security teams spotted …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month