
Automated network pentesting uncovers what traditional tests missed
Most organizations run an annual network penetration test, remediate the issues it uncovers, and move on. But attackers are probing networks every day, using publicly …

Deepfakes are rewriting the rules of geopolitics
Deception and media manipulation have always been part of warfare, but AI has taken them to a new level. Entrust reports that deepfakes were created every five minutes in …

Garak: Open-source LLM vulnerability scanner
LLMs can make mistakes, leak data, or be tricked into doing things they were not meant to do. Garak is a free, open-source tool designed to test these weaknesses. It checks …

Fixing silent failures in security controls with adversarial exposure validation
Organizations often operate as if their security controls are fully effective simply because they’re deployed, configured, and monitored. Firewalls are in place, …

AI agents are here, now comes the hard part for CISOs
AI agents are being deployed inside enterprises today to handle tasks across security operations. This shift creates new opportunities for security teams but also introduces …

CISOs, stop chasing vulnerabilities and start managing human risk
Breaches continue to grow in scale and speed, yet the weakest point remains unchanged: people. According to Dune Security’s 2025 CISO Risk Intelligence Survey, over 90 percent …

Plex tells users to change passwords due to data breach, pushes server owners to upgrade
Media streaming company Plex has suffered a data breach and is urging users to reset their account password and enable two-factor authentication. “An unauthorized third …

Fake npm 2FA reset email led to compromise of popular code packages
Malicious versions of at least 18 widely used npm packages were uploaded to the npm Registry on Monday, following the compromise of their maintainer’s account. …

Download: Cyber defense guide for the financial sector
Data breaches cost more for financial organizations than they do for those in many other industries. In attempting to strengthen your financial organization’s …
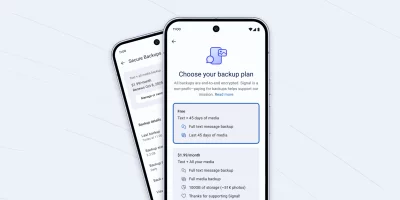
Signal adds secure backup option for chat history
Losing a phone can mean losing years of conversations. Signal is rolling out a new secure backup feature to help users keep their messages safe without giving up privacy. The …

Nearly 500 researchers urge EU to rethink controversial CSAM scanning proposal
Nearly 500 scientists and researchers have signed an open letter warning that the latest version of the EU’s Chat Control Proposal would weaken digital security while failing …

Ongoing malvertising campaign targets European IT workers with fake GitHub Desktop installers
Researchers have spotted a malvertising (and clever malware delivery) campaign targeting IT workers in the European Union with fake GitHub Desktop installers. “We …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month