
One-time SMS links that never expire can expose personal data for years
Online services often treat one-time links sent by text message as low-risk conveniences. A new study shows that these links can expose large amounts of personal data for …

More employees get AI tools, fewer rely on them at work
People across many organizations now have access to AI tools, and usage keeps spreading. Some groups rely on AI during regular work, others treat it as an occasional helper. …

Agentic AI edges closer to everyday production use
Many security and operations teams now spend less time asking whether agentic AI belongs in production and more time working out how to run it safely at scale. A new Dynatrace …
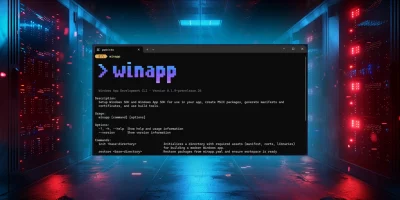
Microsoft introduces winapp, an open-source CLI for building Windows apps
Microsoft has released winapp, a new command line interface aimed at simplifying the process of building Windows applications. The open-source tool targets developers who rely …

New infosec products of the week: January 23, 2026
Here’s a look at the most interesting products from the past week, featuring releases from cside, Obsidian Security, Rubrik, SEON, and Vectra AI. cside targets hidden website …

Energy sector orgs targeted with AiTM phishing campaign
Organizations in the energy sector are being targeted with phishing emails aimed at compromising enterprise accounts, Microsoft warns. The attack campaign The attacks started …

Tesla, Sony, and Alpine systems compromised on day one of Pwn2Own Automotive 2026
Security researchers uncovered 37 previously unknown vulnerabilities on the opening day of Pwn2Own Automotive 2026, earning a combined $516,500 in prize money, according to …

OpenWrt One gains support for running Debian
Debian now runs on the OpenWrt One hardware platform following recent engineering work by Collabora. OpenWrt One is a developer focused router designed to support embedded …

Exposed training apps are showing up in active cloud attacks
Security teams often spin up vulnerable applications for demos, training, or internal testing. A recent Pentera research report documents how those environments are being left …

Unbounded AI use can break your systems
In this Help Net Security video, James Wickett, CEO of DryRun Security, explains cyber risks many teams underestimate as they add AI to products. He focuses on how fast LLM …

The internet’s oldest trust mechanism is still one of its weakest links
Attackers continue to rely on domain names as an entry point into enterprise systems. A CSC domain security study finds that large organizations leave this part of their …

A new framework helps banks sort urgent post-quantum crypto work from the rest
Financial institutions now have a concrete method for deciding where post-quantum cryptography belongs on their security roadmaps. New research coordinated by Europol sets out …
Featured news
Resources
Don't miss
- Fake Claude Code install pages highlight rise of “InstallFix” attacks
- Decoding silence: How deaf and hard-of-hearing pros are breaking into cybersecurity
- Turning expertise into opportunity for women in cybersecurity
- Open-source tool Sage puts a security layer between AI agents and the OS
- Iran-linked APT targets US critical sectors with new backdoors