
Meta AI in WhatsApp organizes chats and reopens privacy issues
The trend of integrating AI into digital platforms continues. In the latest Android beta release (2.26.9.4), the company has introduced a feature that allows users to organize …

NATO greenlights iPhone and iPad for classified information handling
Apple confirmed that the iPhone and iPad have been approved for use with classified information in NATO restricted environments. The devices will no longer require special …

Android app uses Bluetooth signals to detect nearby smart glasses
Smart glasses with built-in cameras are showing up in more public spaces, and a growing number of people want a way to know when one is nearby. An Android app called Nearby …

Samsung’s Galaxy S26 turns privacy into a visible and invisible feature
The Samsung Galaxy S26 series is out, offering plenty of security features that protect personal data while providing users with transparency and control over how their …

Reddit fined $19.5 million for failing to protect children’s personal data
The UK’s Information Commissioner’s Office (ICO) has fined Reddit $19.5 million after finding that the company failed to use children’s personal information lawfully, exposing …

Apple privacy labels often don’t match what Chinese smart home apps do
Smart home devices in many homes collect audio, video, and location data. The apps that control those devices often focus on the account owner, even when the technology also …

Google Search introduces new ways to remove sensitive personal information and explicit images
Google expanded its “Results about you” tool to give users more control over sensitive personal information and added a way to request removal of non-consensual explicit …
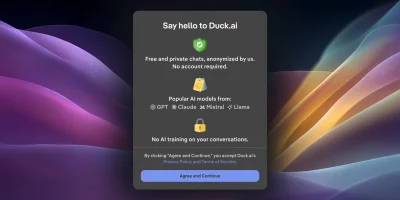
DuckDuckGo enables AI voice chat without saving voice data
DuckDuckGo has added voice chat to Duck.ai, allowing users to speak to an AI assistant while keeping audio private, unrecorded, and excluded from AI training. Voice chat is …

Face scans and ID checks are coming to Discord
Discord users will soon see a change to how their accounts work. From early March 2026, access to some features will require age verification using an ID or a face scan. The …

OpenAI updates Europe privacy policy, adding new data categories
OpenAI has updated its Europe-facing privacy policy following the November 2024 EU revision, clarifying scope, expanding coverage, and detailing user controls. The updated …

Mobile privacy audits are getting harder
Mobile apps routinely collect and transmit personal data in ways that are difficult for users, developers, and regulators to verify. Permissions can reveal what an app can …

Smart glasses are back, privacy issues included
AI smart glasses are the latest addition to fashion, and they include a camera, a microphone, AI, and privacy risks. After Google Glass failed to gain traction more than a …
Featured news
Resources
Don't miss
- Your dependencies are 278 days out of date and your pipelines aren’t protected
- Security debt is becoming a governance issue for CISOs
- BlacksmithAI: Open-source AI-powered penetration testing framework
- When cyber threats start thinking for themselves
- IronCurtain: An open-source, safeguard layer for autonomous AI assistants