mobile security

Western governments lay the groundwork for secure 6G networks
Governments are preparing for 6G, the next generation of mobile networks, placing security and resilience among their top priorities. In response, seven countries …

Motorola turns to GrapheneOS for smartphone security upgrade
Motorola is strengthening smartphone security through a long-term partnership with the GrapheneOS Foundation, a mobile security nonprofit that develops a hardened operating …

NATO greenlights iPhone and iPad for classified information handling
Apple confirmed that the iPhone and iPad have been approved for use with classified information in NATO restricted environments. The devices will no longer require special …

Samsung’s Galaxy S26 turns privacy into a visible and invisible feature
The Samsung Galaxy S26 series is out, offering plenty of security features that protect personal data while providing users with transparency and control over how their …

European Commission hit by cyberattackers targeting mobile management platform
The European Commission’s mobile device management platform was hacked but the incident was swiftly contained and no compromise of mobile devices was detected, …

Samsung tackles shoulder surfing on Galaxy devices
Our phones hold our most personal details, and we use them everywhere. On the bus, in elevators, and while waiting in line, screens are often visible to people nearby. The …
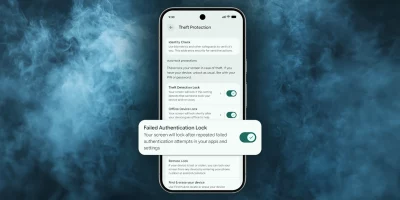
Android just got smarter at stopping snatch-and-run phone thefts
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use. These updates are available on Android …

Uneven regulatory demands expose gaps in mobile security
Mobile networks carry a great deal of the world’s digital activity, which makes operators a frequent target for attacks. A study released by the GSMA shows that operators …

iOS security features you should use to protect your privacy
iOS 18 comes with several privacy and security features that many iPhone users overlook. Knowing how to use them can help you protect your personal information and control …

From cleaners to creepers: The risk of mobile privilege escalation
In this Help Net Security video, Nico Chiaraviglio, Chief Scientist at Zimperium, explores how Android apps can be abused to escalate privileges, giving attackers access to …

44% of mobile users encounter scams every day
Nearly half of of mobile users encounter mobile scams daily, with people in the US and UK more likely to be targeted than those in other regions, according to Malwarebytes. …

Phone theft is turning into a serious cybersecurity risk
Phone theft is a rising issue worldwide, and it’s more than just a property crime. It’s a serious cybersecurity threat. In the UK alone, the Metropolitan Police seizes 1,000 …
Featured news
Resources
Don't miss
- Airbus CSO on supply chain blind spots, space threats, and the limits of AI red-teaming
- The people behind cyber extortion are often in their forties
- Fake Claude Code install pages highlight rise of “InstallFix” attacks
- Decoding silence: How deaf and hard-of-hearing pros are breaking into cybersecurity
- Turning expertise into opportunity for women in cybersecurity