encryption

Quantum security is turning into a supply chain problem
Supplier onboarding, invoice processing, and procurement platforms run on encrypted data flows that were built for long-term trust. In many organizations, that trust still …

Your encrypted data is already being stolen
Quantum computing is often treated as a distant, theoretical cybersecurity issue. According to Ronit Ghose, Global Head, Future of Finance of Citi Institute, that mindset is …

Why secure OT protocols still struggle to catch on
Industrial control system networks continue to run on legacy communication protocols that were built for reliability and uptime, not authentication or data integrity. In many …

EFF calls out major tech companies on encryption promises
The Electronic Frontier Foundation (EFF) has introduced a new campaign called Encrypt It Already, focused on expanding the use of end-to-end encryption in consumer technology …
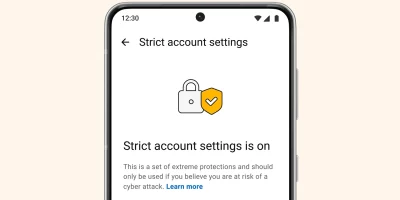
WhatsApp rolls out new security feature to protect users from sophisticated attacks
To add an extra layer of protection to its end-to-end encryption, WhatsApp has begun rolling out a new privacy and security feature called Strict Account Settings. It is …

A new framework helps banks sort urgent post-quantum crypto work from the rest
Financial institutions now have a concrete method for deciding where post-quantum cryptography belongs on their security roadmaps. New research coordinated by Europol sets out …

Let’s Encrypt rolls out 6-day and IP-based certificates
Let’s Encrypt says its short-lived TLS certificates with a 6-day lifetime are now generally available. Each certificate is valid for 160 hours from the time it is issued. To …

Rakuten Viber CISO/CTO on balancing encryption, abuse prevention, and platform resilience
In this Help Net Security interview, Liad Shnell, CISO and CTO at Rakuten Viber, discusses how messaging platforms have become critical infrastructure during crises and …

Duplicati: Free, open-source backup client
Duplicati is an open source backup client that creates encrypted, incremental, compressed backup sets and sends them to cloud storage services or remote file servers. What the …

Manufacturing is becoming a test bed for ransomware shifts
Manufacturing leaders may feel that ransomware risk has settled, but new data shows the threat is shifting in ways that require attention, according to a Sophos report. A …
Product showcase: Tuta – secure, encrypted, private email
Tuta, formerly known as Tutanota, is built for anyone who wants email that stays private. Instead of treating encryption like a bonus feature, the service encrypts almost …

Tor Project is rolling out Counter Galois Onion encryption
People who rely on Tor expect their traffic to move through the network without giving away who they are. That trust depends on the strength of the encryption that protects …
Featured news
Resources
Don't miss
- The CISO view of fraud risk across the retail payment ecosystem
- Applying green energy tax policies to improve cybersecurity
- Microsoft reveals critical Windows Admin Center vulnerability (CVE-2026-26119)
- Data on 1.2 million French bank accounts accessed in registry breach
- Bug in widely used VoIP phones allows stealthy network footholds, call interception (CVE-2026-2329)