Artificial intelligence

GenAI is fueling smarter fraud, but broken teamwork is the real problem
More than 80 percent of large U.S. companies were targeted by socially engineered fraud in the past year, according to Trustmi’s 2025 Socially Engineered Fraud & Risk …

AI isn’t taking over the world, but here’s what you should worry about
In this Help Net Security video, Josh Meier, Senior Generative AI Author at Pluralsight, debunks the myth that AI could “escape” servers or act on its own. He explains how …

AI can’t deliver without trusted, well-governed information
While enterprise IT leaders recognize the transformative potential of AI, a gap in information readiness is causing their organizations to struggle in securing, governing, and …

Agentic AI coding assistant helped attacker breach, extort 17 distinct organizations
Cybercriminals have started “vibe hacking” with AI’s help, AI startup Anthropic has shared in a report released on Wednesday. An attacker used the agentic AI …

ScamAgent shows how AI could power the next wave of scam calls
Scam calls have long been a problem for consumers and enterprises, but a new study suggests they may soon get an upgrade. Instead of a human scammer on the other end of the …

Where security, DevOps, and data science finally meet on AI strategy
AI infrastructure is expensive, complex, and often caught between competing priorities. On one side, security teams want strong isolation and boundaries. On the other, …

How CISOs are balancing risk, pressure and board expectations
AI has moved to the top of the CISO agenda. Three in five CISOs see generative AI as a security risk, with many worried about sensitive data leaking through public tools. At …

AI is becoming a core tool in cybercrime, Anthropic warns
A new report from Anthropic shows how criminals are using AI to actively run parts of their operations. The findings suggest that AI is now embedded across the full attack …

AI Security Map: Linking AI vulnerabilities to real-world impact
A single prompt injection in a customer-facing chatbot can leak sensitive data, damage trust, and draw regulatory scrutiny in hours. The technical breach is only the first …

How compliance teams can turn AI risk into opportunity
AI is moving faster than regulation, and that creates opportunities and risks for compliance teams. While governments work on new rules, businesses cannot sit back and wait. …
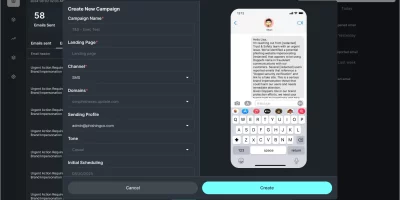
What CISOs can learn from Doppel’s new AI-driven social engineering simulation
Doppel has introduced a new product called Doppel Simulation, which expands its platform for defending against social engineering. The tool uses autonomous AI agents to create …

LLMs at the edge: Rethinking how IoT devices talk and act
Anyone who has set up a smart home knows the routine: one app to dim the lights, another to adjust the thermostat, and a voice assistant that only understands exact phrasing. …
Featured news
Resources
Don't miss
- Airbus CSO on supply chain blind spots, space threats, and the limits of AI red-teaming
- The people behind cyber extortion are often in their forties
- Fake Claude Code install pages highlight rise of “InstallFix” attacks
- Decoding silence: How deaf and hard-of-hearing pros are breaking into cybersecurity
- Turning expertise into opportunity for women in cybersecurity