
PromptSpy: First Android malware to use generative AI in its execution flow
ESET researchers have discovered PromptSpy, the first known Android malware to abuse generative AI as part of its execution flow in order to achieve persistence. This marks …

Firmware-level Android backdoor found on tablets from multiple manufacturers
A new Android backdoor embedded directly in device firmware can quietly take control of apps and harvest data, Kaspersky researchers found. The malware, named Keenadu, was …

Android 17 beta brings privacy, security, and performance changes
Google has released the first beta of Android 17, giving developers an early view of changes to core app behavior, platform tooling, performance, media handling, and …

Mobile privacy audits are getting harder
Mobile apps routinely collect and transmit personal data in ways that are difficult for users, developers, and regulators to verify. Permissions can reveal what an app can …

Google disrupts proxy network used by 550+ threat groups
Google has disrupted Ipidea, a massive residential proxy network consisting of user devices that are being used as the last-mile link in cyberattack chains. “In a single …

Google agrees to pay $135 million over Android data harvesting claims
Google agrees to pay $135 million to settle a proposed class action lawsuit brought by Android smartphone users over alleged unauthorized cellular data transmissions. After …
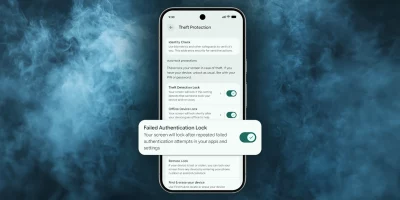
Android just got smarter at stopping snatch-and-run phone thefts
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use. These updates are available on Android …
Product showcase: TrackerControl lets Android users see who’s tracking them
TrackerControl is an open-source Android application designed to give users visibility into and control over the hidden data within mobile apps. Many apps routinely …
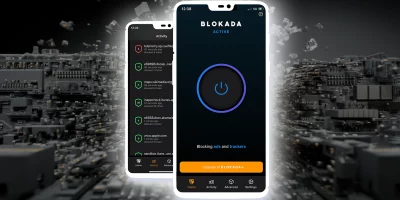
Product showcase: Blokada for Android gives users control over network traffic
Blokada is a network privacy and ad-blocking application available on Android, iOS, Windows, macOS, and Linux. It is designed to reduce ads, block trackers, and limit unwanted …
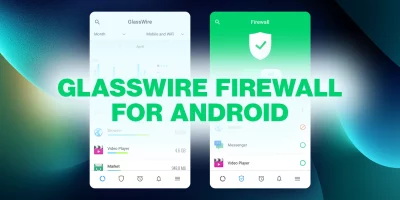
Product showcase: GlassWire mobile firewall for Android
GlassWire is a free network monitoring and security application for Windows and Android. It lets you see how your system communicates over the internet and local network. The …

40 open-source tools redefining how security teams secure the stack
Open source security software has become a key way for teams to get flexibility, transparency, and capability without licensing costs. The free tools in this roundup address …

AI vs. you: Who’s better at permission decisions?
A single tap on a permission prompt can decide how far an app reaches into a user’s personal data. Most of these calls happen during installation. The number of prompts keeps …
Featured news
Resources
Don't miss
- Open-source benchmark EVMbench tests how well AI agents handle smart contract exploits
- Public mobile networks are being weaponized for combat drone operations
- Attackers keep finding the same gaps in security programs
- China-linked hackers exploited Dell zero-day since 2024 (CVE-2026-22769)
- The era of the Digital Parasite: Why stealth has replaced ransomware