Zeljka Zorz

Massive gambling network doubles as hidden C2 and anonymity infrastructure, researchers say
A sprawling network that’s seemingly maintained to serve (illegal) online gambling opportunities and deliver malware to Indonesian citizens is likely also being used to …

Google fixes Android vulnerabilities “under targeted exploitation” (CVE-2025-48633, CVE-2025-48572)
Google has shipped patches for 51 Android vulnerabilities, including two high-severity flaws (CVE-2025-48633, CVE-2025-48572) that “may be under limited, targeted …

How a noisy ransomware intrusion exposed a long-term espionage foothold
Getting breached by two separate and likely unconnected cyber attack groups is a nightmare scenario for any organization, but can result in an unexpected silver lining: the …

Cryptomixer crypto laundering service taken down by law enforcement
German and Swiss law enforcement agencies have taken down Cryptomixer, an illegal cryptocurrency mixer service, and have confiscated over 25 million euros (approximately $29 …

Gainsight breach: Salesforce details attack window, issues investigation guidance
The number of Salesforce customers affected by the recent compromise of Gainsight-published applications is yet to be publicly confirmed, but Salesforce released indicators of …
New “HashJack” attack can hijack AI browsers and assistants
Security researchers at Cato Networks have uncovered a new indirect prompt injection technique that can force popular AI browsers and assistants to deliver phishing links or …

Popular code formatting sites are exposing credentials and other secrets
Widely used code formatting sites JSONFormatter and CodeBeautify are exposing sensitive credentials, API keys, private keys, configuration files and other secrets, watchTowr …
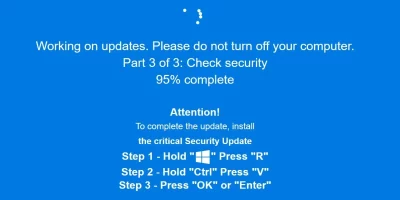
Fake “Windows Update” screen fuels new wave of ClickFix attacks
A convincing (but fake) “Windows Update” screen can be the perfect lure for tricking users into infecting their computers with malware. Add a multi-stage delivery …

Salesforce Gainsight compromise: Early findings and customer guidance
In the wake of Salesforce’s announcement about “unusual activity involving Gainsight-published applications” and the company’s revocation of access and …

Salesforce investigates new incident echoing Salesloft Drift compromise
In what may be a repeat of the Salesloft Drift supply chain compromise, Salesforce confirmed that they’ve identified unusual activity involving Gainsight-published apps …

Security gap in Perplexity’s Comet browser exposed users to system-level attacks
There is a serious security problem inside Comet, the AI-powered agentic browser made by Perplexity, SquareX researchers say: Comet’s MCP API allows the browser’s …

MacOS DigitStealer malware poses as DynamicLake, targets Apple Silicon M2/M3 devices
A new infostealer is targeting macOS users by masquerading as the legitimate DynamicLake UI enhancement and productivity utility and possibly Google’s Drive for desktop app. …
Featured news
Resources
Don't miss
- FreeScout vulnerability enables unauthenticated, zero-click RCE via email (CVE-2026-28289)
- As AI agents start making purchases, security teams must rethink risk
- Engineering trust: A security blueprint for autonomous AI agents
- Webinar: The True State of Security 2026
- Over 1,200 IceWarp servers still vulnerable to unauthenticated RCE flaw (CVE-2025-14500)