EU telecoms suffered 169 major security incidents in 2017
ENISA, EU’s agency for network and information security, has released a report on major telecom security incidents that occurred in the EU in 2017.
About the report
Electronic communication providers in the EU have to report significant security incidents to the national telecom regulatory authorities (NRAs) in 28 EU Member States, Norway and Switzerland.
The providers are currently required to report incidents causing disruptions to fixed and mobile telephony, fixed and mobile Internet access, and other services, but will soon also be required to report other security breaches (e.g., confidentiality breaches).
Every year, the NRAs report summaries about the most significant incidents, based on a set of agreed thresholds. ENISA’s report gives an aggregated overview of these summaries.
Key findings
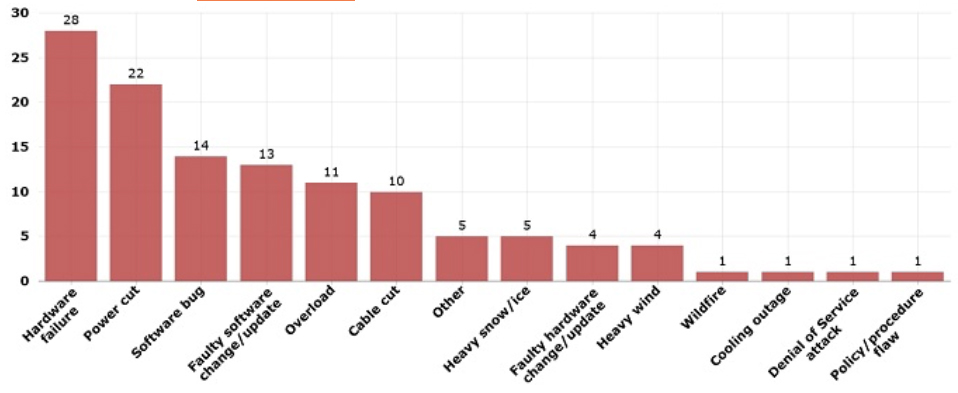
There have been 169 major telecom security incidents in 2017. Of these:
- 62,1% were due to system failures (hardware failures, software bugs or faulty software updates).
- 18,3% were caused by human errors
- 17,2% were caused by natural phenomena
- 2,4% were caused by malicious actions (e.g., DoS attack disrupting the service, cable theft).
Most incidents have an impact on mobile telephony and internet, and this incidents impact, on average, most users.
In 2017 human errors was the root cause category involving most users affected per incident (around 1.2 million user connections on average), and incidents caused by natural phenomena had by far the longest average recovery time (96 hours vs 13 hours for human errors and system failures) and the highest number of user hours lost.
These extraordinary results for incidents due to natural phenomena is an exception, the agency says, as it’s due to the last year’s wildfires. But natural phenomena will definitely continue to be a concern for telecom providers across the EU, with extreme weather becoming more common due to climate change.
Incidents caused by malicious actions are rare. Only a small percentage of reported incidents (2.5% in 2017) was categorized as caused by malicious actions. This percentage reduced by half compared to the previous year (5.1% in 2016).
How incident reporting helps providers
“The incident reporting that you see in this report is the tip of the iceberg – in a positive sense. The fine-grained incident reporting that happens at a national level is really what is driving supervision,” say Ilias Bakatsis and Marnix Dekker, the authors of the report.
“Incident reports trigger a conversation between the national regulator and the sector, about what causes outages and what can be done to prevent them. Of course, the bulk of the incidents, the daily issues, are often uninteresting: something broke, a software bug, etc. Telecom providers deal with such issues on a daily basis. But sometimes you do see interesting issues pop up. Like for instance the issue with accidental cable cuts by machinery which was reported frequently some years ago. Many EU countries now have platforms and tools that help to avoid such cable cuts, often set up as public-private partnerships.”
Steve Purser, head of the operations department at ENISA, says that the report shows that when you strike the right balance, breach reporting can be very useful, not only for the regulatory authorities and the policy makers but also for the private sector itself.
“Of course the incident reporting in itself does not solve any problems, but it does give a good indication of where effort needs to go in terms of preventing future incidents. One of the major learning points from this report (and previous reports) is that the causes of major outages are rarely malicious but are due to more mundane issues such as poorly written software or incorrect configuration,” he notes.