Android DoubleLocker ransomware encrypts data, changes device PIN
A new piece of ransomware is targeting Android users. Dubbed DoubleLocker, it both encrypts users’ files and changes the device’s PIN.
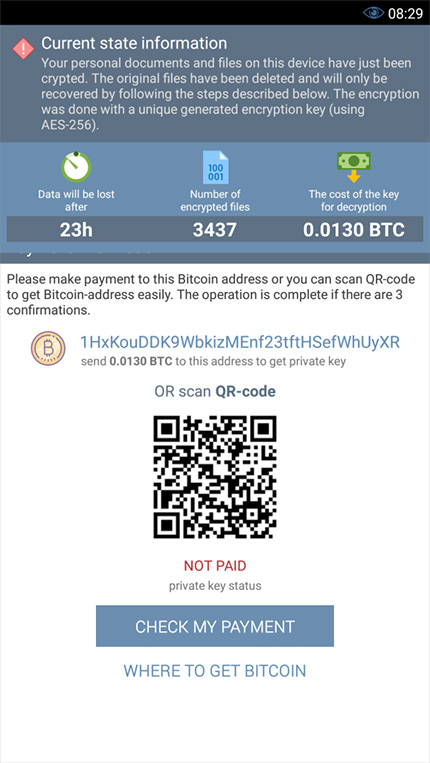
About DoubleLocker
Lukáš Štefanko, the ESET researcher who discovered the ransomware, says that it is based on the BankBot Android Trojan.
Like its “parent,” DoubleLocker is distributed mostly through compromised Web sites, masked as a Adobe Flash Player update. Unlike BankBot, it doesn’t harvest users’ banking credentials.
“Once launched, the app requests activation of the malware’s accessibility service, named ‘Google Play Service’. After the malware obtains the accessibility permissions, it uses them to activate device administrator rights and set itself as the default Home application, in both cases without the user’s consent,” ESET’s Urban Schrott explained. This means that the ransomware is activated every time the user clicks on the home button.
Once persistence is achieved, DoubleLocker first changes the device’s PIN to a random value, then encrypts all files from the device’s primary storage directory.
“The new PIN is set to a random value which the attackes neither store nor send anywhere, so it’s impossible for the user or a security expert to recover it. After the ransom is paid, the attacker can remotely reset the PIN and unlock the device,” says Schrott.
The ransomware uses AES encryption to encrypt the files and there is no way to reverse the process without the right key, which is in possession of the crooks. They are asking 0.0130 BTC (currently around $72) for it.
Protection against DoubleLocker
By now, many mobile AV solutions should catch this malware before it does its dirty work, but all users would do well to think twice about installing apps or updates randomly pushed on them.
Having a recent backup will save the victims from paying the ransom, because removing DoubleLocker is as easy as performing a factory reset of the device.
Users who have rooted their devices can bypass the PIN lock without a factory reset, but only if the device was in the debugging mode before the ransomware got activated.
“If this condition is met, then the user can connect to the device by ADB and remove the system file where the PIN is stored by Android. This operation unlocks the screen so that the user can access their device. Then, working in safe mode, the user can deactivate device administrator rights for the malware and uninstall it. In some cases, a device reboot is needed,” Schrott notes.
Unfortunately, the encrypted data is still uncoverable without the decryption key.