Investigation reveals large botnet hiding behind Fast Flux technique
Fast Flux, a DNS technique first introduced in 2006 and widely associated with the Storm Worm malware variants, can be used by botnets to hide various types of malicious activities – including phishing, web proxying, malware delivery, and malware communication.
The technique allows the botnet to “hide” behind an ever-changing network of compromised hosts, ultimately acting as proxies and making detection incredibly difficult.

High-level architecture overview of the Fast Flux network and associated threat landscape
Akamai conducted an analysis of a sophisticated botnet using Fast Flux techniques made up of more than 14,000 IP addresses. Although most of the IP addresses originate from eastern Europe, some of the associated IP addresses are in address space that is assigned to Fortune 100 companies. These addresses are most likely used by this particular Fast Flux network owner as spoofed entities and are not genuine members of the network.
This approach allows the botnet to “borrow” the positive reputation associated with the IP address to carry out its malicious activities.
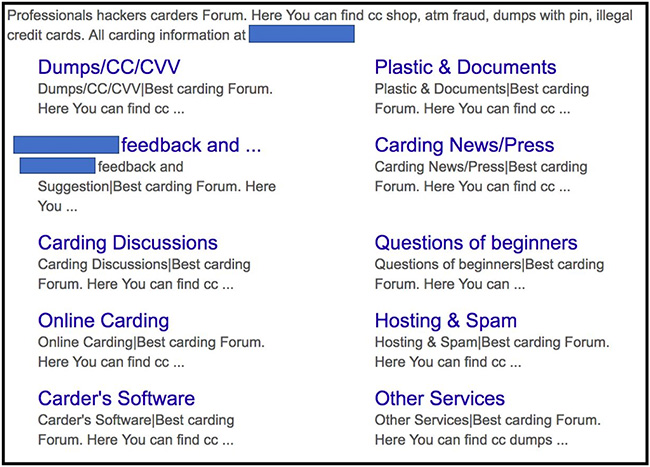
Example for illegal-market website catalog, hosted on the hosting network
“The increasing complexity of enterprise networks and dependencies on public networks make it more difficult than ever to maintain an accurate picture of what is really happening on your networks,” said Or Katz, Principal Lead Security Researcher, Akamai.
“At the same time, the increasing sophistication of the obfuscation techniques used by hackers to hide their malicious activities makes it even more important to maintain granular insights into network activity. The level of visibility Akamai has into both ‘good’ and ‘bad’ traffic on the Internet and within corporate enterprise network makes this kind of research possible and is critically important to how we can best protect our customers,” Katz concluded.
The findings of Akamai’s are compiled in a new white paper – Digging Deeper – An In-Depth Analysis of a Fast Flux Network.