Third party trackers on web shops can identify users behind Bitcoin transactions
More and more shopping Web sites accept cryptocurrencies as a method of payment, but users should be aware that these transactions can be used to deanonymize them – even if they are using blockchain anonymity techniques such as CoinJoin.
Two attacks
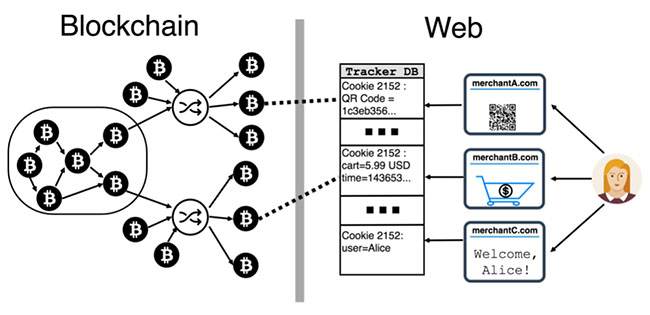
Independent researcher Dillon Reisman and Steven Goldfeder, Harry Kalodner and Arvind Narayanan from Princeton University have demonstrated that third-party online tracking provides enough information to identify a transaction on the blockchain, link it to the user’s cookie and, ultimately, to the user’s real identity.
“Based on tracking cookies, the transaction can be linked to the user’s activities across the web. And based on well-known Bitcoin address clustering techniques, it can be linked to their other Bitcoin transactions,” they noted.
Add to this the fact that many merchants additionally leak users’ PII such as name or email address to trackers, and if becomes obvious that trackers can easily link the transaction to a user’s web profile and identity.
But, until know, it was possible to believe that using mixing technique such as the aforementioned CoinJoin or other types of coin mixing would prevent the linkage of Bitcoin addresses to user’s identity. Unfortunately, that’s not true.
“We show that a small amount of additional information, namely that two (or more) transactions were made by the same entity, is sufficient to undo the effect of mixing. While such auxiliary information is available to many potential entities — merchants, other counterparties such as websites that accept donations, intermediaries such as payment processors, and potentially network eavesdroppers — web trackers are in the ideal position to carry out this attack,” they pointed out.
The researchers also analyzed the Web sites of 130 online merchants that accept Bitcoin as payment, and found that:
- 53 of the 130 leak payment information to third parties (mostly intentionally, for advertising and analytics purposes)
- 17 of the 130 send the receiving Bitcoin address or BTC- denominated price to a third party
- 43 of the 130 send some form of non-BTC-denominated cart price data to third parties
- 28 of the 130 shared add-to-cart events with third parties
- 49 of the 130 leak some form of PII to a total of 137 third parties, and 21 of those third parties also receive transaction-relevant information.
How can users protect themselves?
Using browser extensions such as uBlock Origin, Adblock Plus, or Ghostery to block trackers does not provide fullproof protection, particularly if the adversary is a network eavesdropper or the payment processor. And using improved mixing techniques, such as multi-round mixing, is only partially effective.
For now, the researchers believe that switching to using another cryptocurrency is a better option.
“Unlike the Bitcoin approach of anonymity as an overlay, other cryptocurrencies bake privacy into the protocol, and promise untraceability of transactions,” they noted.
“The most well known of these are Zcash, based on the Zerocash protocol, and Monero, based on the Cryptonote protocol. Zcash is more computationally expensive but comes with more rigorous security properties. Of the two, Monero has more vendor support at the time of writing, but still far less than Bitcoin or even Litecoin, and primarily on hidden-service sites merchandising illicit goods. While some anonymity weaknesses have recently been revealed in Monero, we believe that it is not susceptible to the cluster intersection attack.”