Bad security habits persist, despite rising awareness
While 82 percent of respondents believe the IT security industry is making progress against cyber attacks, those gains are undercut by egregious security practices in critical areas such as privileged account security, third-party vendor access and cloud, according to CyberArk.
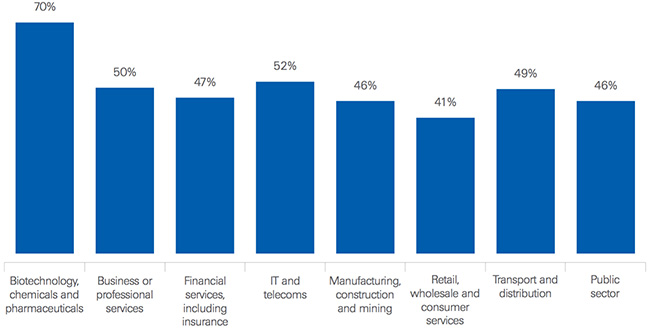
Which industries allow third-party vendors (supply chain, IT management rms, etc.) remote access to internal networks?
Bad security habits persist
Headline-making cyber attacks have driven significant increases in cyber security awareness. However, the failure to turn increased awareness into the enforcement of security best practices undermines progress for organizations’ cyber security efforts.
79 percent state their organization has learned lessons from major cyber attacks and has taken appropriate action to improve security.
- 67 percent now believe their CEO/board of directors provide sound cyber security leadership (up from 57 percent in 2015).
- The top actions taken because of this awareness are deployment of malware detection (25 percent), endpoint security (24 percent) and security analytics (16 percent).
55 percent of respondents state their organization has changed or evolved processes for managing privileged accounts. Despite this, 40 percent of organizations still store privileged and admin passwords in a Word document or spreadsheet, while 28 percent use a shared server or USB stick.
49 percent of organizations allow third-party vendors (such as supply chain and IT management firms) remote access to their internal networks. While the majority of respondents secure and monitor that access, the public sector has the least third-party vendor access controls in place compared to other industries, with 21 percent not securing and 33 percent not monitoring that activity.
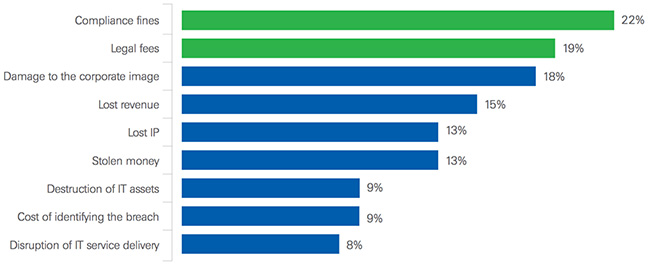
How does your organization estimate the cost of a data breach and what is not included in the cost of a breach?
Striking a balance between fear and overconfidence
Organizations are increasingly adopting a post-breach mindset, preparing to deal with ongoing cyber attacks and activity in the case of a breach. This preparedness is leading to positive steps in post-breach planning, but concerns exist about how overconfidence may affect the ability to protect against cyber attacks.
Three out of four IT decision makers now believe they can prevent attackers from breaking into their internal network – up from 44 percent in 2015.
- Despite this, 36 percent believe a cyber attacker is currently on their network, or has been in the last 12 months.
- 46 percent believe their organization was a victim of a ransomware attack in the past two years.
82 percent of respondents believe the security industry in general is making progress against cyber attacks. 17 percent believe the industry is falling further behind. Nearly every organization (95 percent) has a cybersecurity emergency response plan. This preparedness is undermined by a lack of communication and testing – only 45 percent communicate and regularly test their plan with all IT staff.
68 percent of organizations cite losing customer data as one of their biggest concerns following a cyber attack.
- 60 percent of those who use the cloud store customer data in it.
- 57 percent who store information in the cloud are not completely confident in their cloud provider’s ability to protect their data.
When identifying the most difficult stage of a cyber attack to mitigate, malware installation ranked first (41 percent), followed by privileged account takeover (25 percent).
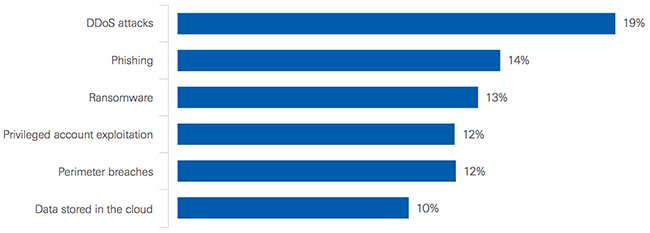
In the next 12 months, what types of cyber attacks or tactics do you think are the number one concern for your organization?
Future risks emerge
As cyber attacks continue on trusted institutions such as government, utilities and financial systems, respondents identify what types of cyber attacks or tactics are most concerning. Respondents also share which cyber attack scenarios they think represent the most immediate and potentially catastrophic threat in general.
Respondents list the following types of cyber attacks or tactics as the top-ranked concern in the next 12 months: DDoS attacks (19 percent), phishing (14 percent), ransomware (13 percent), privileged account exploitation (12 percent) and perimeter breaches (12 percent).
Attacks on financial systems, including disruption of global markets (58 percent) is the most potentially catastrophic threat perceived by respondents, followed by attacks causing massive utilities damage (55 percent) and those impacting civil services such as healthcare and hospital services (51 percent).
The impact of a breach on customer data and corporate accountability
The survey found a varied global picture in terms of preparedness for increased regulatory oversight and the impact on cyber security programs and accountability.
While 70 percent of global respondents agree that the threat of legal action and fines influence the level of executive/board involvement in security-related decisions, 22 percent of the respondents do not incorporate compliance fines or legal fees (19 percent) into the cost of a breach.
Nearly seven in ten (69 percent) respondents state that, in response to a breach or cyber attack, stopping the breach/removing the attackers is among their top priorities, followed by detecting the source of the breach (53 percent).