Corporate espionage for dummies: HP scanners
Web servers have become commonplace on just about every hardware device from printers to switches. Such an addition makes sense as all devices require a management interface and making that interface web accessible is certainly more user friendly than requiring the installation of a new application. Despite typically being completely insecure, such web servers on printers/scanners are generally of little interest from a security perspective, even though they may be accessible over the web, due to network misconfigurations. Yes, you can see that someone neglected to replace the cyan ink cartridge but that’s not of much value to an attacker. However, that’s not always the case.
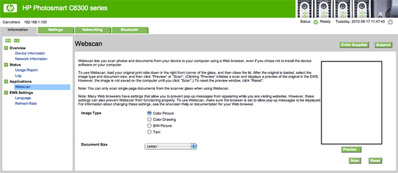
One Version of the WebScan interface on an HP scanner
I was recently looking at a newer model of an HP printer/scanner combo and something caught my eye. HP has for some time, embedded remote scanning capabilities into many of their network aware scanners, a functionality often referred to as Webscan. Webscan allows you to not only remotely trigger the scanning functionality, but also retrieve the scanned image, all via a web browser. To make things even more interesting, the feature is generally turned on by default with absolutely no security whatsoever.
The insider threat
With over $1B in printer sales in Q3 2010 alone, and with many of those devices being all-in-one printers, running across an HP scanner in the enterprise is certainly very common. What many enterprises don’t realize, is that their scanners may by default allow anyone on the LAN to remotely connect to the scanner and if a document was left behind, scan and retrieve it using nothing more than a web browser. Ever left a confidential document on the scanner and sprinted back to retrieve it when you realized? Thought so.
Want to know if your office LAN has any wide open HP scanners running? Run this simple Perl script to to determine if there are any devices on the local network running HP web servers.
As everything is web based, an enterprising but disgruntled employee could simply write a script to regularly run the scanner in the hopes of capturing an abandoned document. The URL used to send the web scanned documents to a remote browser is also completely predictable as shown:

A script could therefore also be written to run once per second to capture any documents scanned using the Webscan feature.
The external threat
It’s bad enough that many enterprises are running scanners that are remotely accessible by rogue employees, but what if those same scanners were accessible to anyone on the Internet? Whether intentionally set up as such or more likely accidentally exposed via a misconfigured network, there are numerous scanners exposed on the Internet, the majority of which are not password protected. In fact, HP kindly lets you know on the home page if sensitive functionality is password protected, by displaying the Admin Password status alongside other status information such as printer ink levels and the current firmware version. Interestingly, based on the sample set examined, there was a greater likelihood that HP Photosmart scanners were not locked down as opposed to Officejet scanners. This finding actually makes sense, given that Officejet scanners tend to be marketed to corporate users, a group that is hopefully more likely to implement security protections on hardware/software.

Example Google/Bing queries used to identify open scanners:
- “Estimate only. Actual ink levels may vary.”
- inanchor:”page=printerInfo”
- “Estimated Ink Levels” “HP Photosmart” “Items Needing Attention”
- hp photosmart status “product serial number” “product model number”
- inurl:index.htm?cat=info&page=printerInfo
- inbody:”Estimated Black Ink Level”.
The many variations of the HP web interface ensures that no single query will identify all exposed scanners, but as can be seen, with a little creativity, it is trivially easy to find exposed scanners.
The wall of shame
What sort of things do people leave on their scanners? In researching this article, I saw checks, legal documents, completed ballot forms, phone numbers… and my personal favorite, Jim’s diploma informing the world that he’s now a Certified Mold Inspector – congratulations Jim!
Here are samples of documents remotely retrieved due to corporations using HP scanners that were not password protected, on misconfigured networks that exposed their scanners to the Web.