Ransomware attacks escalate, companies largely unprepared
Ransomware attacks against endpoints have recently taken place against hospitals in the US and Germany. Attacks have increased in severity to the point that the FBI issued an alert asking businesses for help in the fight against ransomware.
The Ponemon Institute surveyed 694 U.S. IT security practitioners who are involved in endpoint security in a variety of organizations.
Key findings
Laptops pose the biggest endpoint threat to enterprises: Forty-three percent of organizations believe laptops are the biggest endpoint threat, followed by Smartphones at 30 percent, Tablets at 19 percent and USB sticks at six percent.
Mobile devices are believed to be the faster growing threat: Eighty-six percent of respondents believe that mobile devices such as smart phones (Android, iPhone, Blackberry) are the greatest risk.
The most unsecured desktop and mobile operating systems: Twenty-eight percent of respondents believe that Android is the most unsecured, Windows was second at 23 percent, iOS was third at 19 percent.
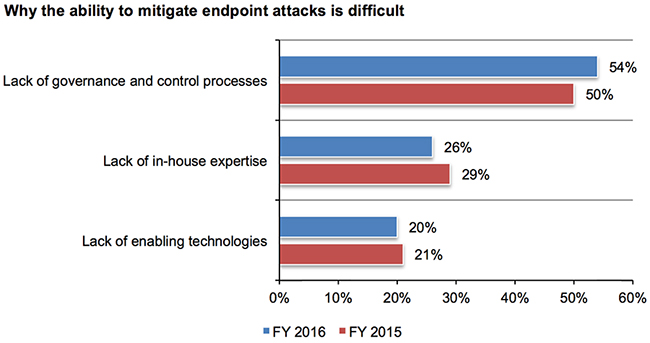
Organizations face a more difficult time enforcing endpoint security policies: Thirty-five percent of organizations believe enforcing their own endpoint security policies have become more difficult in 2016 versus only 31 percent in 2015. In total, 71 percent of respondents find it difficult to enforce.
Endpoint devices connected to the network aren’t all secured: Surprisingly, nearly one third of respondents (28 percent) said that half or more of the endpoint devices connected to their network aren’t secured. Three percent of respondents said none of the devices are secured.
Certain applications increase vulnerabilities and IT risk: Sixty-two percent of respondents believe that Adobe applications pose the biggest threat to endpoints, and Java applications was second at 54 percent.

“Hackers are relentless, they won’t take ‘no’ for an answer and unless you have mechanisms in place to either slow them down or stop attacks against your endpoints, your data and IP is at serious risk,” said Michael Davis, CTO, CounterTack. “What is most concerning is that the malware used widely in today’s attacks give a hacker complete access to an organization’s data not just the device. Long gone are the days of simple fraud and identity theft as the main attacker goal. This endpoint study is a clear call to action for organizations of any size that if hacked, your data will be targeted, sold and distributed and the only way to prevent that from happening is to secure the devices accessing your data-endpoints.”