40% of orgs running VMware still susceptible to Heartbleed
More than three months have passed since the discovery of the OpenSSL Heartbleed bug, and many systems are still vulnerable.
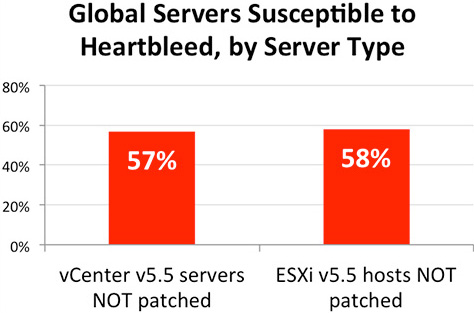
According to data collected by data analytics company CloudPhysics, more than half of deployed VMware vCenter servers (57%) and ESXi hypervisor hosts (58%) affected by the flaw are still unpatched.
VMware has done a good job pushing out security updates for its products (including those above mentioned) that fixed the vulnerability in the two weeks following the discovery, so the problem here are the administrators of the virtual datacenters.
“I speculate that IT teams are more lax about patching ESXi since those machines are typically behind the firewall and not easy to reach from the outside world,” noted Irfan Ahmad, co-founder and CTO at CloudPhysics.
“However, that laxity doesn’t make the delay in patching a good idea. For one thing, insider attacks continue to be a major source of breaches. Another consideration is that if outside attackers do manage to infiltrate a low privilege service inside your firewall, you have just given them carte blanche to attack your most sensitive data.”
All in all, their data says that a high 40 percent of the organizations in its global user base have at least one vCenter server or ESXi host that is still vulnerable.
“Many security experts have predicted that it could take months to years to finally get rid of Heartbleed. Sadly, at least for VMware infrastructure, this seems to be true,” he says, as the rate of patching is continually slowing down.