Map of state data breach notification laws
Current state data breach notification laws are strikingly similar but vary in compliance requirements for businesses, with all laws highlighting the need for companies to deploy methods for closely storing, protecting and controlling sensitive information.
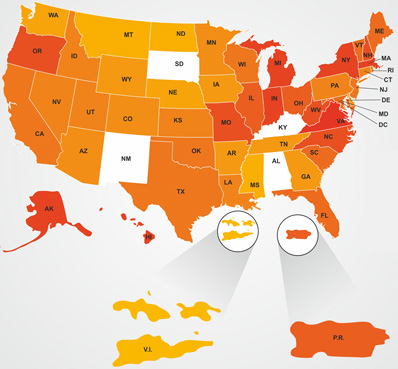
Imation used publicly available sites (including information obtained via the National Conference of State Legislatures) to analyze state compliance laws in the 46 U.S. states that have such laws, as well as in Puerto Rico, the District of Columbia and the U.S. Virgin Islands.
Imation created a “Compliance Heat Map” to depict the strictness of data breach laws and resulting penalties for breaches. The Compliance Heat Map provides a visual snapshot of the strictness of regulations by state, using a color scale ranging from light yellow (less strict) to dark red (more strict).
IT pros today are responsible for managing data, which includes ensuring security, business continuity and regulatory compliance. For small- to mid-sized businesses, the challenge is often to meet compliance requirements with limited resources, which leads to higher risk.
Imation’s research found most state data breach notification laws to offer similar definitions of personally identifiable information and requirements regarding the notification of affected parties. Among the research’s noteworthy findings:
- Four states have yet to enact a data breach notification law: Alabama, Kentucky, New Mexico and South Dakota.
- According to Imation’s analysis, Virginia has the most strict law in the nation. The law provides specific requirements on what is to be included in a breach notification, requires government and credit reporting agency notification, and includes a large financial penalty relative to other states.
- A few states, including Virginia, require notification even if breached data is encrypted—if the encrypted data was stolen along with the encryption keys.
To conduct the research, Imation applied to the laws a series of questions, organized to evaluate the laws’ requirements regarding encryption, data that is within scope of the laws, notification of data loss and destruction of data, as well as penalties for non-compliance with the laws.
Imation also considered other germane laws, such as those dictating data destruction or allowing for consumer freezing of credit report requests. Imation used publicly available information about the laws, including the legislation itself.