Firesheep countermeasure tool BlackSheep
 Firesheep is the Firefox extension that makes it easier to steal logins and take over social media and email accounts after users log in from a WiFi hotspot or even their own unprotected network.
Firesheep is the Firefox extension that makes it easier to steal logins and take over social media and email accounts after users log in from a WiFi hotspot or even their own unprotected network.
Developers say they were simply hoping to shed light on the problem of not using SSL encryption for user sessions. But the temptation for people to use it for nefarious purposes is too great.
Zscaler researchers have created, and are now offering to every consumer, a free Firefox plugin called BlackSheep, which serves as a counter-measure. BlackSheep combats Firesheep by monitoring traffic and then alerting users if Firesheep is being used on the network.
BlackSheep does this by dropping “fake’ session ID information on the wire and then monitors traffic to see if it has been hijacked.
While Firesheep is largely passive, once it identifies session information for a targeted domain, it then makes a subsequent request to that same domain, using the hijacked session information in order to obtain the name of the hijacked user along with an image of the person, if available.
It is this request that BlackSheep identifies in order to detect the presence of Firesheep on the network. When identified, the user will be receive the following warning message:
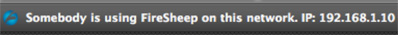
It should be noted that Firesheep and BlackSheep cannot be installed on the same Firefox instance as they share much of the same code base. If you want to run both Firesheep and BlackSheep on the same machine, they should be installed in separate Firefox profiles.
By default, BlackSheep generates fake traffic every 5 minutes. You can change this value in the option settings.