Malware peddlers exploit fear of Android Installer Hijacking bug
The recently disclosed existence of the “Android Installer Hijacking” vulnerability is being exploited by malware and adware peddlers and online survey scammers, warns Trend Micro.
The attackers don’t exploit the bug, but are taking advantage of the worry Android users feel regarding its existence.
When the vulnerability was disclosed to the public in late March, Palo Alto Networks offered a free vulnerability scanner app called Installer Hijacking Scanner that checks whether a device is affected by the bug (half of them initially were).
This app is used as a lure on at least one website:
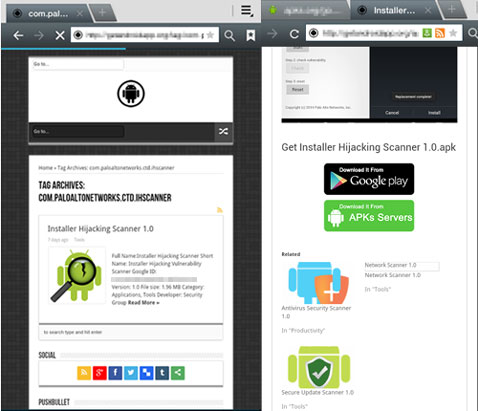
Curiously enough, clicking on the two download buttons will take users to the official Google Play page of the scanner app, but clicking anywhere else on the site will get users redirected either to sites with online surveys or fake software updates.
At the same time, a file will be automatically downloaded onto the device: an SMS Trojan, adware, or even a legitimate app.
The researchers also found two other similar sites. One of them, leading to another suspicious site, was often down, and they believe this is an attempt to make it fly under the radar. The other one redirects to a third site that pops-up a window saying that the visitor’s phone is infected with “(13) Virus!”
No files are automatically downloaded from both of these sites, and in the latter example, the pop-up window stays up even if the user clicks on the OK button or closes the browser. The tab in which the site was opened also persists every time the browser is re-opened.
“Taking advantage of a hot topic or current event is par for the course for social engineering,” Trend Micro fraud analyst Gideon Hernandez notes, and advises: “Users should always visit reputable sites to get their information. To download fixes for vulnerabilities and other threats, it’s always best to go to the developer or an official source.”