60% of Android attacks use financial malware
Malicious programs targeting Android-based devices in order to steal money were used in 60 percent of attempted attacks registered by Kaspersky Lab security products, according to a survey by Kaspersky Lab and INTERPOL between August 2013 and July 2014
These cybercriminals frequently targeted Android users in Russia, but also in Ukraine, Spain, United Kingdom, Vietnam, Malaysia, Germany, India and France.
In absolute terms, there were more than 588,000 Android users worldwide who faced financial malware attacks (Trojan-SMS and Trojan-Banker) during the reporting period. That is six times greater than the number from the equivalent period 12 months earlier.
Overall, 57.08 percent of all reported incidents involved attacks utilizing programs from the Trojan SMS malware family. These programs are designed to send messages to short premium-rate numbers without the owner’s knowledge. Russia received the greatest number of Trojan SMS attacks with 64.42 percent of all Kaspersky Lab anti-virus detections registered on devices of users from this country. About a quarter of Trojan-SMS attacks were detected in Kazakhstan (5.71%), Ukraine (3.32%), Spain (3.19%), the UK (3.02%), Vietnam (2.41%), Malaysia (2.3%), Germany (2%), India (1.55%) and France (1.32%).
Another 1.98 percent of attacks used Trojan-Banker malware which, when combined with Trojan-SMS functionality, can steal bank card data as well as user names and passwords for online banking services. Russia is on top of this chart as well with 90.58 percent of all Trojan-Banker detections registered on the territory of the Russian Federation. The rest of the top 10 all had a relatively small level of attacks and included Kazakhstan, Ukraine, Belarus, USA, Lithuania, Azerbaijan, Bulgaria, Germany and Uzbekistan.
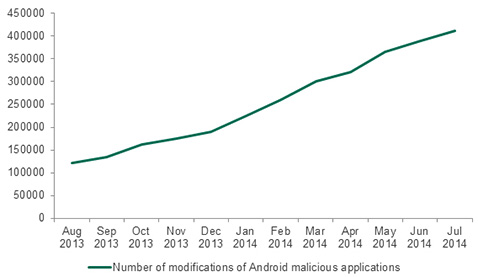
Although during the reporting period Kaspersky Lab registered relatively few attacks using mobile banking Trojans, experts found the number of mobile malware modifications grew sharply – from 423 in August 2013 to 5,967 in July 2014 – a 14-fold increase.
Modifications are a version of a malicious program that is slightly altered from the original piece of malware. This small change can make the malware less noticeable to antivirus solutions. The high level of modification growth found during this study shows that cybercriminals were creating multiple variations of their malware in attempts to go undetected by antivirus solutions and infect as many devices as possible. Typically, antivirus companies will create a new signature within the software to defend against this type of tactic.
“A successful Trojan-Banker infection can give a fraudster access to all of the victim’s money, while a Trojan-SMS needs to infect dozens or even hundreds of devices to show a worthwhile profit. In addition, not all owners currently use mobile online banking applications. That’s why there is such a difference in the number of Trojan-SMS and Trojan-Banker attacks registered by our products,” said Roman Unuchek, senior virus analyst at Kaspersky Lab.
“During the past few years we have witnessed the rise of mobile cyber threats which have become more complex and intelligent enough to target specific entities. With the mobile market growing exponentially, it is clearer that these threats are mutating to include new attack vectors allowing the exploitation of personal smart devices,” said Madan Oberoi, director of Cyber Innovation & Outreach at INTERPOL’s Global Complex for Innovation.