Fake AV served to Dailymotion visitors via malicious ads
The extremely popular video-sharing website Dailymotion (dailymotion.com) has been found serving malicious ads that trigger fake infection warnings and try to make visitors install a fake AV solution.
This malware delivery campaign has been spotted on Tuesday by researchers from security company Invincea, who analysed the attack and the malware in question, and have notified Dailymotion of the problem. Hopefully, the matter has been resolved by now.
The attack unfolded as follows: visitors to the site would be automatically redirected via Javascript to a website sporting the fake infection warning, which would then automatically serve the fake AV (guard-cerq.exe) for download.
If the victim fell for the trick and installed the malware, the system would get rebooted and, upon starting again, would show a fake “active scan” window and ultimately scary scan results.
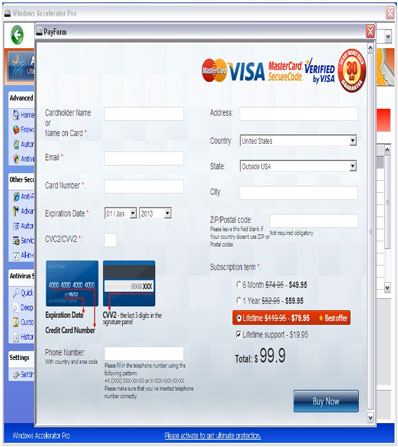
Users who then opted to remove all the “found” malware were urged to pay $100 for the pleasure (click on the screenshot to enlarge it):
Also, do we need to mention that all the information – including the credit card number, expiration date and CVV number – is harvested by the crooks behind the scheme for later exploitation?
The malware also prevents all network communication until the victim pays up so, in a way, you may say that this fake AV is also part ransomware.
The researchers haven’t said whether Dailymotion has blocked the malware-serving ads, but my guess that is they probably have by now.
The bad news about this entire situation is that Dailymotion is visited by around 17 million visitors per month, and the fake AV in question – Windows Accelerator Pro – was initially detected by just a handful of legitimate AV solutions, so the “body count” in this particular case could be considerable.