Infosec products of the month: September 2021
Here’s a look at the most interesting product releases from September, featuring releases from Attivo Networks, Absolute, Anomali, Alation, Citrix, Cloudflare, Cyware, Code42, Commvault, CoSoSys, Druva, DataDome, deepwatch, Elastic, Fugue, ForgeRock, Hornetsecurity, IPKeys Power Partners, IDrive, McAfee, Nutanix, Palo Alto Networks, Query.AI, Qualys, Red Sentry, Stairwell, ThreatConnect and Titania.


Absolute DataExplorer enables IT and security teams to capture critical endpoint data
The Absolute DataExplorer tool enables administrators to answer key questions about their employees’ endpoints with the ability to expand data capture and reporting beyond what is typically available through standard device and security management tools, without requiring professional services or advanced coding skills.


Anomali XDR features extend visibility over a wider range of threat information sources
New XDR features and enhancements provide customers with the ability to align global threat intelligence with organizational security goals, extend visibility and integration over a wider range of threat information sources, detect threats with greater precision, and further optimize their response.

Query.AI’s enhancements drive efficiencies in cybersecurity investigations
The Query.AI platform serves as a connective tissue that delivers federated search to conduct investigations across data silos and eliminates the antiquated approach of universal data centralization.


Cyware CTIX Spoke allows ISAC/ISAO members to take necessary actions on ingested threat intelligence
CTIX Spoke is purpose-built to offer an accessible threat intelligence module for ISAC/ISAO members interested in operationalizing threat indicators (IOCs) shared by their ISACs/ISAOs and other threat intelligence feed sources.


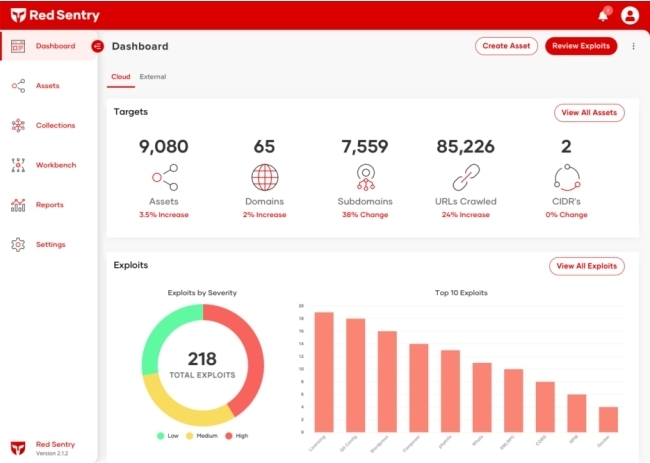
Red Sentry’s pentesting platform automates penetration tests and runs them continuously
Red Sentry automatically identifies and tracks all of an organization’s online assets via its attack surface analysis platform. Red Sentry provides continuous pentests on a subscription basis as Software as a Service (SaaS), and the company offers manual pentests as well.

Code42 Incydr Flows accelerates incident response for insider risk events
Fully integrated into the Code42 Incydr product, Flows are automated to accelerate insider risk response and reduce the workloads of often overburdened security teams. At a time when employees average 13 data exposure events per user per day, security teams require scalable solutions that balance reducing insider risk with the business need for collaboration.


Commvault announces ransomware services to help businesses tackle growing cyber threats
The Commvault Ransomware Response Service provides the expertise and resources to help recover from an attack. As part of the service, Commvault provides a Ransomware Recovery Incident Manager backed by the Commvault Recovery Operations team. The service works with customers to identify and recover critical data and expedite a return to normal business operations.


Attivo Networks ThreatStrike functionality helps hide real credentials from attacker tools
The Attivo ThreatStrike cloaking hides and denies unauthorized access to applications. For example, only Chrome will have access to its credential store, and all other applications won’t. The product launches with support for 75 of the most popular Windows applications that attackers target, with a plan to add more applications in the future.


ForgeRock Autonomous Identity helps enterprises reduce risk and manage workforce access
The company’s AI-driven approach to identity governance and administration (IGA) offers new capabilities to help teams heighten security by avoiding excessive access permissions and eliminating orphaned user accounts — both prime targets for external attackers and insider threats.


IPKeys Power Partners SigmaFlow Beacon helps organizations align with NERC compliance mandates
The SigmaFlow Beacon provides one, purpose-built solution for NERC baseline management, collecting the critical cyber data in real time and seamlessly incorporating the approval process within the SigmaFlow workflow and evidence platform.
![]()

Qualys Patch Management keeps endpoints up to date to reduce risk from exploits
Qualys is integrating zero-touch patching capabilities into Qualys Patch Management. Zero-Touch Patch ensures that companies’ endpoints and servers are proactively updated as soon as patches are available, reducing their overall attack surface.


Hornetsecurity launches security and data loss prevention solution for Microsoft 365
365 Total Protection Enterprise Backup enables automatic backup and recovery of an organization’s Microsoft 365 mailboxes, Teams, SharePoint and OneDrive, as well as backing up the data in users’ Windows-based endpoints such as laptops or Windows workstations.


Palo Alto Networks Okyo Garde protects work-from-home employees and small businesses
For larger companies looking to protect employees who are working from home, Okyo Garde will be integrating with Prisma Access, Palo Alto Networks’ cloud-delivered security platform. By combining Okyo Garde and Prisma Access, corporations will be able to extend their corporate networks and bring unified security policy management and SASE to work-from-home employees.


ThreatConnect 6.3 helps organizations identify and remediate threats faster
ThreatConnect unifies the actions of the security team around the most critical risks, supports their response with streamlined and automated workflows, and strengthens the entire security ecosystem through powerful technology integrations.


Titania’s module automates the audit process for mission critical CMMC security practices
The new module automates the audit process for dozens of the most mission critical CMMC security practices for the core network. It produces a CMMC assessor-ready report that indicates compliance within minutes and provides a list of priorities and remediation advice to address any issues.

IDrive 360 enables entire machine backups for businesses
Ideal for businesses of any size, IDrive 360 enables IT departments to oversee data protection for their entire company, allowing them to implement backup plans for units, groups, or individual devices. This ensures that every bit of data generated by endpoint devices is backed up and ready to be recovered in case of a data loss disaster.


Alation Data Governance App accelerates data governance using ML and AI
The Alation Data Governance App supports enterprises on their data governance journey with its people-centric approach. It utilizes machine learning and automation to accelerate and scale data governance while removing the drudgery of data stewardship processes.


CoSoSys Endpoint Protector 5.4.0.0 enables users to override a DLP policy
Endpoint Protector 5.4.0.0 brings a host of new features to customers, including support for user remediation, and the ability to use the Azure AD API in Microsoft Graph to synchronize user profiles.


McAfee’s online protection service protects information across all online activities
With an emphasis on providing identity and privacy for all, the new McAfee service is full of enhancements, including McAfee Identity Protection Service delivered via the new web-based McAfee Protection Center to over 28 million McAfee Total Protection and McAfee LiveSafe customers; McAfee’s Protection Score available in 32 countries; and a completely redesigned all-in-one mobile app – McAfee Security – which is being launched in over 245 countries globally.


Nutanix Cloud Platform improves support for mission-critical workloads with AOS 6 software
Customers adopting the Nutanix Cloud Platform with AOS 6 gain access to new Business Continuity and Disaster Recovery (BCDR) capabilities previously only found in specialized solutions.

Stairwell Inception helps organizations to get ahead of the most sophisticated attackers
Inception treats all files as suspicious and pre-preserves them as evidence to speed up detection and uncover previously unknown compromises. By continuously evaluating the entirety of evidence in light of emerging insights, it unlocks time—detecting compromise across the past, present, and future states of an organization’s environment, and denying attackers the advantages on which they depend.


Druva introduces curated recovery technology for accelerated ransomware recovery
Druva Curated Recovery mitigates the impact of a ransomware attack, building an uncorrupted, unencrypted and malware-free recovery point to ensure a successful recovery before one is ever initiated.


Elastic expands its threat prevention capabilities to stop advanced threats at the endpoint
Elastic announced expanded Limitless Extended Detection and Response (XDR) capabilities across the Elastic Security solution in its 7.15 release, including new layers of prevention for Windows, macOS and Linux, and host isolation for cloud-native Linux environments.


Cloudflare announces free email offerings to prevent phishing and increase security
Cloudflare announced its entry into email security with new offerings to help solve email challenges. Now, users will be able to create custom email addresses, manage incoming email routing, and prevent email spoofing and phishing on outgoing emails—all for free.


DataDome enhances its online fraud and bot management solution
The new version of DataDome Online Fraud & Bot Management combines new insights with established customer favorites in a new interface and notification platform. With one click, users can now dive into each attack to better understand its trajectory and report back with actionable insights around cyber threats.


deepwatch MDR Essentials strengthens protection against cyber threats for MSBs
With deepwatch MDR Essentials, organizations can deploy a high performance, automated security operations center (SOC) in less than one hour that seamlessly integrates with the existing environment without requiring additional hardware or consulting.


Fugue IaC platform empowers cloud teams to eliminate security gaps
Powered by a Unified Policy Engine, Fugue IaC saves cloud teams significant time and ensures consistent policy enforcement that eliminates the security gaps and wasted effort that come with using separate policies for IaC security and cloud security posture management (CSPM).


Citrix App Delivery and Security Service automates the app delivery process in real-time
Citrix App Delivery and Security Service is designed to help IT transform app delivery from a slow, manual process based largely on guesswork into an efficient, automated one driven by intent so they can gain the agility needed to keep pace with the business and deliver meaningful outcomes.


