New infosec products of the week: August 27, 2021
Here’s a look at the most interesting product releases from the past week, featuring releases from ARMO, Palo Alto Networks, Guardicore, Radiflow and Ermetic.


Kubescape helps admins manage Kubernetes securely
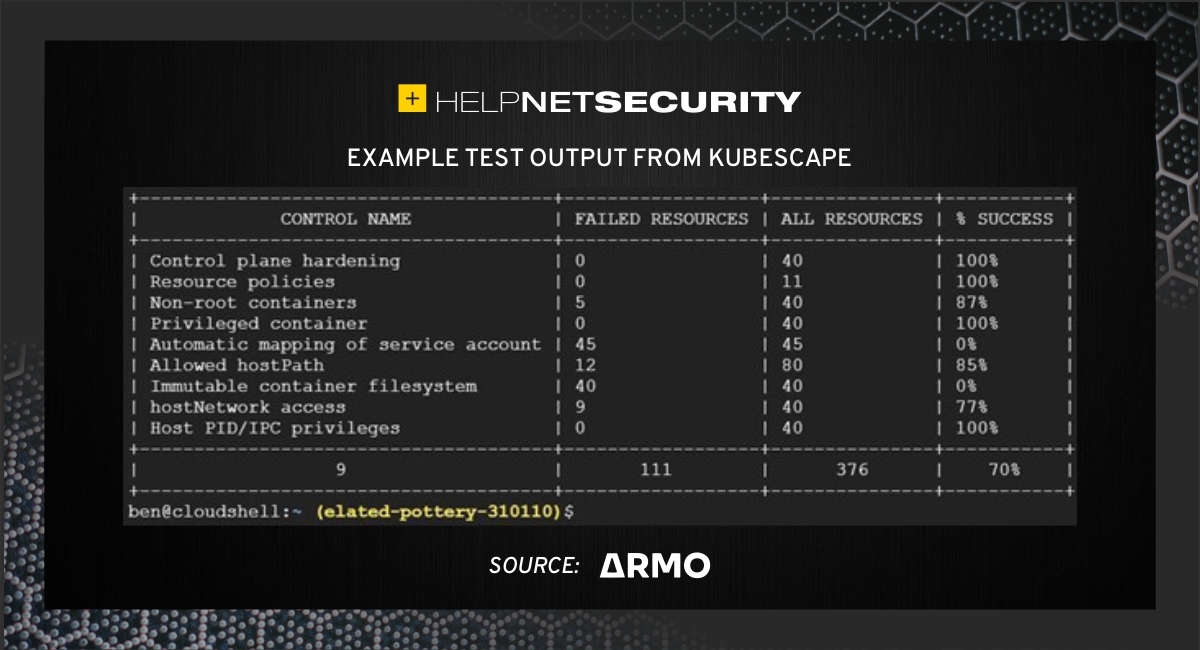
Kubescape is an open-source tool for testing if Kubernetes is deployed securely, as defined in the recently released Kubernetes Hardening Guidance by NSA and CISA. Kubescape is easy to use and the results can be delivered in print (see image below) or can be retrieved in JSON format.

Palo Alto Networks Cortex XDR 3.0 automates threat detection and investigation across cloud environments
The third generation of Cortex XDR offers SOC teams even broader protections across their attack surface. By extending detection, monitoring and investigation into cloud environments, and detecting malicious user activities and insider threats through analysis of identity data, SOC teams benefit from security analytics across endpoint, network, cloud and identity for organization-wide detection and response.


Guardicore Centra enables security teams to stop ransomware and lateral movement
Guardicore Centra enables security teams to protect against lateral movement in ransomware attacks with software-based segmentation. Enterprises gain a single, scalable platform with real-time threat detection and response capabilities to detect lateral movement and minimize dwell time throughout the entire cyberattack kill chain.


Radiflow’s risk management platform for OT facilities allows CISOs to view all their sites on one dashboard
This latest Radiflow CIARA software release offers a non-intrusive breach attack simulator that takes into account the business importance of each site so the CISO can find the most vulnerable points on their industrial automation networks across all their sites, allowing them to practice the most effective mitigation tools.


Ermetic Platform combines CIEM and CSPM capabilities in one integrated solution
Combining CIEM and CSPM provides 365 degree context to automate the detection and remediation of cloud security risks. For example, understanding whether a sensitive data store is vulnerable to attack requires a holistic assessment of its access permissions, resource configuration and network configuration.