Malware family integration across botnets
Analysis by Symantec reveals that in February, 1 in 290.1 emails (0.345%) was malicious making February among the most prolific time periods both in terms of simultaneous attacks and malware family integration across Zeus (aka Zbot), Bredolab and SpyEye.

Also in February, there were at least 40 variants of malware associated with the Bredolab Trojan, accounting for at least 10.3 percent of email-borne malware blocked by MessageLabs Intelligence in February. These latest findings reveal that contrary to recent beliefs, Bredolab is not dead and techniques previously associated with Bredolab malware have now become more common among other major malware families.
Since the end of January, MessageLabs Intelligence has tracked significant volumes of collaborative attacks that make use of well-timed and carefully crafted targeted techniques. As February began, the attacks increased in number and these malware families were used aggressively to conduct simultaneous attacks via propagation techniques, signaling the likelihood of a common origin for these infected emails.
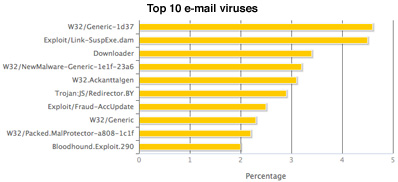
Although the vast majority of attacks were related to Zeus and SpyEye, many of the attacks share commonalities with the well-known Bredolab Trojan, indicating some of the features associated with Bredolab were being used by Zeus and SpyEye.
All of these attacks made use of a ZIP archive attachment that contained an executable comprising the malware code. In February, 1.5% of malware blocked comprised ZIP archive attachments and further analysis revealed that 79.2% of this was connected with the latest wave of Bredolab, Zeus and SpyEye attacks.
Over the past year, malicious executable files have increased in frequency along with PDF files, the most popular file format for malware distribution. PDFs now account for a larger proportion of document file types used as attack vectors.
In 2009, approximately, 52.6 percent of targeted attacks used PDF exploits, compared with 65 percent in 2010, an increase of 12.4 percent. Despite a downturn this month, if the trend were to continue as it has over the past year, 76 percent of targeted malware could be used for PDF-based attacks by mid-2011.
Geographical trends:
- China became the most spammed in February with a spam rate of 86.2 percent.
- In the US and Canada, 81.4 percent of email was spam. Spam levels in the UK were 81.1 percent.
- In The Netherlands, spam accounted for 82.2 percent of email traffic, while spam levels reached 81.2 percent in Germany, 81.7 percent in Denmark and 81.0 percent in Australia.
- Spam levels in Hong Kong reached 82.8 percent and 80.4 percent in Singapore. Spam levels in Japan were 78.5 percent. In South Africa, spam accounted for 81.6 percent of email traffic.
- South Africa remained the most targeted by email-borne malware with 1 in 81.8 emails blocked as malicious in February.
- In the UK, 1 in 139.0 emails contained malware. In the US virus levels were 1 in 713.6 and 1 in 328.8 for Canada. In Germany, virus levels reached 1 in 393.1, 1 in 451.1 in Denmark and 1 in 910.4 for The Netherlands.
- In Australia, 1 in 365.8 emails were malicious and, 1 in 455.3 for Hong Kong, for Japan it was 1 in 1,331.0 compared with 1 in 828.9 for Singapore and 1 in 457.0 for China.