All Zoom users get end-to-end encryption (E2EE) option next week
Starting next week, Zoom users – both those who are on one of the paid plans and those who use it for free – will be able to try out the solution’s new end-to-end encryption (E2EE) option.
In this first rollout phase, all meeting participants:
- Must join from the Zoom desktop client, mobile app, or Zoom Rooms
- Must enable the E2EE option at the account level and then for each meeting they want to use E2EE for

How does Zoom E2EE work?
“Zoom’s E2EE uses the same powerful GCM encryption you get now in a Zoom meeting. The only difference is where those encryption keys live,” the company explained.
“In typical meetings, Zoom’s cloud generates encryption keys and distributes them to meeting participants using Zoom apps as they join. With Zoom’s E2EE, the meeting’s host generates encryption keys and uses public key cryptography to distribute these keys to the other meeting participants. Zoom’s servers become oblivious relays and never see the encryption keys required to decrypt the meeting contents.”
The option will be available as a technical preview and will work for meetings including up to 200 participants. In order to join such a meeting, they must have the E2EE setting enabled.
For the moment, though, enabling E2EE for a meeting means giving up on certain features: “join before host”, cloud recording, streaming, live transcription, Breakout Rooms, polling, 1:1 private chat, and meeting reactions.
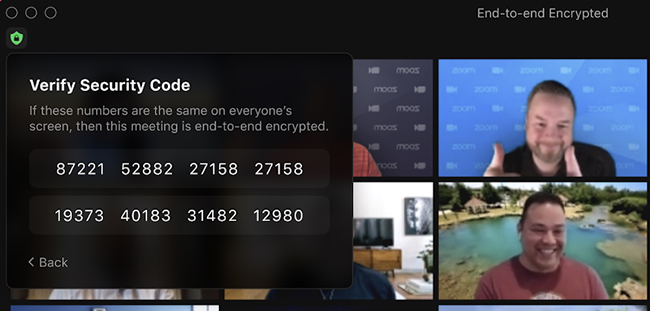
“Participants will also see the meeting leader’s security code that they can use to verify the secure connection. The host can read this code out loud, and all participants can check that their clients display the same code,” the company added.
E2EE for everybody
In June 2020, Zoom CEO Eric Yuan announced the company’s intention to offer E2EE only to paying customers, but after a public outcry they decided to extend its benefits to customers with free accounts as well.
“Free/Basic users seeking access to E2EE will participate in a one-time verification process that will prompt the user for additional pieces of information, such as verifying a phone number via text message. Many leading companies perform similar steps to reduce the mass creation of abusive accounts,” the company reiterated again with this latest announcement.