Credential exposure report: Poor password habits still pose a serious threat
9,050,064,764 credentials have been recovered throughout 2019 which came from a total of 640 unique data breaches and include email addresses connected to plaintext passwords and usernames with plaintext passwords, SpyCloud reveals.
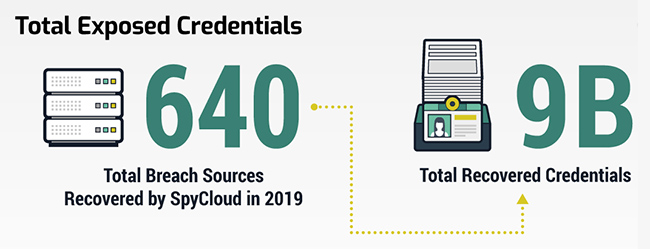
That means, on average, each of these data breaches gave criminals more than 14 million sets of login credentials. Because people often reuse passwords across several accounts, both personal and for work, each set of login credentials could be used to access dozens or more accounts through which cybercriminals can perpetrate fraud.
Credential exposure report
Almost a third of internet users affected by data breaches last year had reused a password in some form. 94% of those who recycled passwords reused the exact same password, while the other 6% made minor changes such as capitalizing the first letter or adding numbers to the end of their typical password. These tactics are easily defeated by tools, which test for common, slight variations.
In terms of organizational security, there’s a worrying trend more of the data criminals are sharing and selling came from breaches of misconfigured or unsecured servers. Organizations may also be taking incomplete steps to protect passwords.
Criminals still using passwords they stole in 2012
The researchers found that more than half (53.7%) of the plaintext passwords recovered were originally protected using the outdated hashing algorithms SHA-1 and MD5.
Security professionals have recommended against using SHA-1 since about 2005, and against using MD5 since as far back as 1996, because cybercriminals can easily and quickly crack passwords hashed with these functions and recover plaintext passwords.
“Our data shows that consumers are still not changing their poor password habits, yet we know they’re holding organizations accountable for their security.” said David Endler, chief product officer for SpyCloud.
“Criminals are still using passwords they stole in 2012 to attack and take over accounts today. Companies need to guide users to set better passwords at the time of account creation and they need to help users maintain strong, uncompromised passwords whenever their credentials are exposed in a breach anywhere in the world.”

World’s most popular passwords protecting some 125 million accounts
Despite the problem of password fatigue and reuse coming into clearer focus over the past few years, little has changed in the world’s most popular passwords. Among the more than nine billion collected last year, the top three are “123456,” “123456789,” and “qwerty,” and are being used to protect some 125 million accounts.
It is increasingly up to organizations to comply with NIST’s password guidelines, which recommend checking user passwords for those that have exposed bee in previous breach corpuses, as well as commonly used or easy-to-guess passwords.