Spying the spy: How to turn Trojans against criminals
“Researchers do vulnerability research on so many various application, why not to do it on this one?” asked himself Andrzej Dereszowski, founder and director of Signal 11, a Polish firm focused on analyzing information leakage incidents and their prevention.
In his research paper titled Targeted attacks: From being a victim to counter attacking, he describes (shortly) common targeted attacks and analyzes the remote administration tools (Trojans) that are used to control the victim’s computer.
Using a particular incident as an example, he manages to identify the software being used through analysis of traffic, behavior, and code. This analysis makes is possible for him to identify potential vulnerabilities in the code that could be used for a counter-attack aimed at the attacker.
Identifying the Trojan in question as Poison Ivy, he analyzes the code, the architecture and the communication in depth and decides to use a reverse engineering framework on part of the code to and performs “process stalking”, i.e. traces the process and marking the stages. Analysis of the program proves that the encrypted communications are done properly and that the vulnerability (if there is any) must be in the deeper levels.
“I decided to fuzz the communication protocol in the way that I let the successful authentication occur, and after that, I allow talking server to client but I randomly modify bytes in the communication stream BEFORE the comms get encrypted. I also need to watch Poison Ivy client; if it crashes, that means I have possibly found a bug,” writes Dereszowski.
His gambit pays off, and the Poison Ivy client crashes when certain byte in the initial message following successful authentication, has been modified:
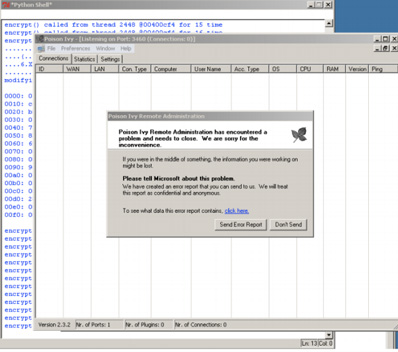
He even manages to write an exploit for the vulnerability, although he doesn’t make the code public for security reasons. But, he explains some techniques he used to make it work, and it makes for a fascinating read – not to mention that it gives hope for an offensive against criminals.