Cybercriminals using custom phishing tools to target the world’s largest tech brands
Cybercriminals are using enterprise-based development and deployment strategies, such as phishing as a service (PaaS), to leverage some of the world’s largest tech brands, with 42.63% of domains observed targeting Microsoft, PayPal, DHL, and Dropbox, according to Akamai.
The report details that phishing is no longer just an email-based threat, but has expanded to include social media and mobile devices, creating a wide-reaching problem that touches all industries. This evolving method continues to morph into different techniques, one of which being BEC attacks.
According to the FBI, BEC attacks resulted in worldwide losses of more than $12 billion between October 2013 and May 2018.
“Phishing is a long-term problem that we expect will have adversaries continuously going after consumers and businesses alike until personalized awareness training programs and layered defense techniques are put in place,” said Martin McKeay, Editorial Director of the State of the Internet/Security report for Akamai.
The report shows that cybercriminals are targeting top global brands and their users across various industries through highly-organized and sophisticated phishing kit operations.
Top targets
During the research period, with 6,035 domains, and 120 kit variations, high technology was the top industry targeted by phishing. Following that, financial services, with 3,658 domains and 83 kit variants, was the second most-targeted industry.
E-Commerce (1,979 domains, 19 kit variants) and media (650 domains, 19 kit variants) rounded out the list. In all, more than 60 global brands were targeted during the reporting period.
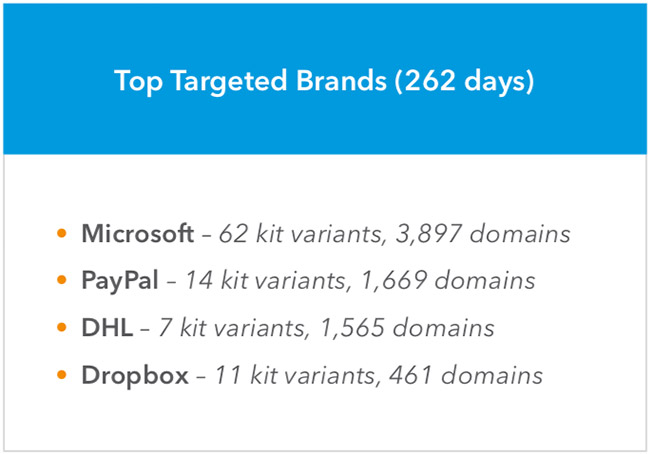
According to Akamai’s monitoring, Microsoft, PayPal, DHL, and Dropbox were the top targeted brands when it came to phishing, with Microsoft taking up 21.88% of total domains (3,897 domains and 62 kit variants), PayPal taking up 9.37% of total domains (14 kit variants), DHL (7 kit variants) taking up 8.79% of total domains and Dropbox having 2.59% (11 kit variants) of total domains.
Criminals continue to adapt
Phishing defenses have forced changes to criminal operations, as they seek to remain undetected for as long as possible. According to the research, 60% of the phishing kits observed were active for 20-days or less during the reporting period, which is becoming more common among phishing attacks. This short lifespan is likely why criminals continue to develop new evasion methods to keep their kits undetected.
The report also discusses a research project that followed the daily operations of a phishing-kit developer who offered three types of kits with advanced evasion techniques, design, and geo-targeting options.

The low prices and top-tier brand targets in these kits are an attractive item, creating a low-barrier for entry into the phishing market for criminals looking to set up shop.
McKeay concludes, “As the phishing landscape continues to evolve, more techniques such as BEC attacks will develop, threatening a variety of industries across the globe. The style of phishing attacks is not one size fits all; therefore, companies will need to do due diligence to stay ahead of business-minded criminals looking to abuse their trust.”