Microsoft’s Attack Surface Analyzer now works on Macs and Linux, too
Microsoft has rewritten and open-sourced Attack Surface Analyzer (ASA), a security tool that points out potentially risky system changes introduced by the installation of new software or configuration changes.
About Attack Surface Analyzer
The initial version of the tool (v1.0, aka “classic”) was released in 2012 and worked only on Windows. It can still be downloaded, but is not supported any longer.
This newest version (v.2.0) is built using .NET Core 2.1 and Electron, and can be used on supported Windows and Windows Server versions, macOS (10.12+) and a number of Linux distros.
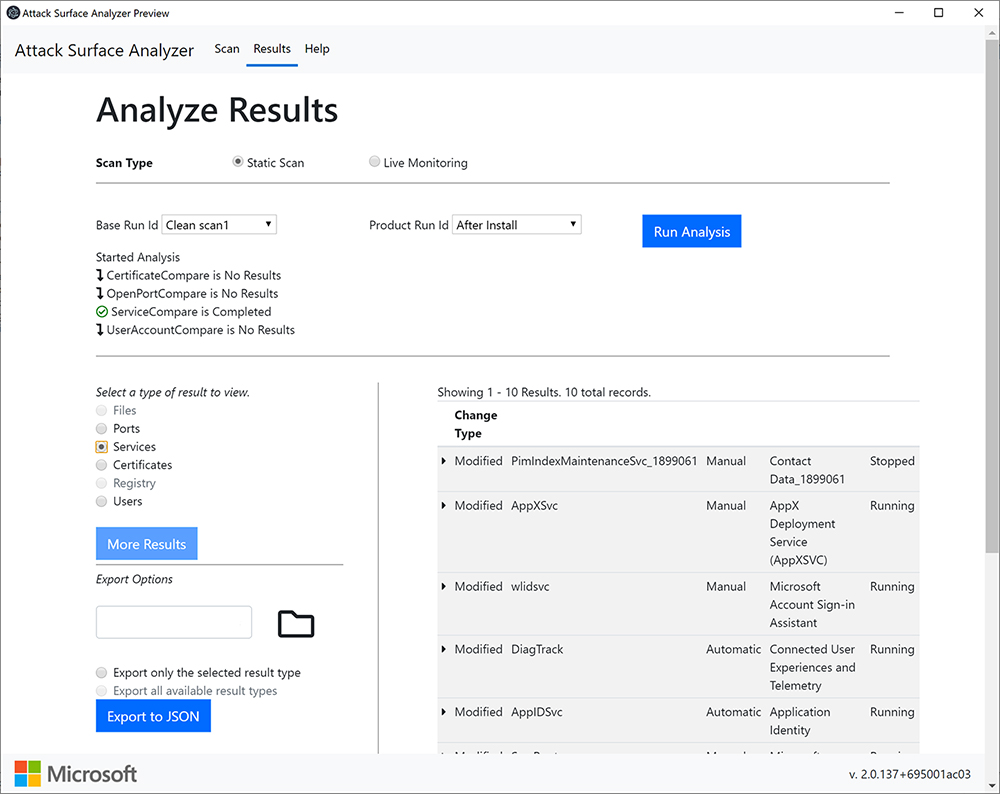
It comes with a command line (CLI) and an Electron-based graphical (GUI) interface and requires administrator privileges to work efficiently and accurately.
“The core feature of Attack Surface Analyzer is the ability to ‘diff’ an operating system’s security configuration, before and after a software component is installed. This is important because most installation processes require elevated privileges, and once granted, can lead to unintended system configuration changes,” Microsoft explains.
Attack Surface Analyzer currently reports on changes to the following operating system components: file system, user accounts, services, network ports, certificates, and registry (Windows only). All data collected is stored in a local SQLite database.”
The tool is easy to use: you install it on the system you want tested, do a baseline scan, install the app you want tested and then scan the system again (product scan). The report created from the collected data will show the changes made to the system.
“There are two options for collection of data: Static or Live. Static is selected by default and will collect indicated information for analysis. For a Live snapshot enter the directory you want monitored and click Scan,” Microsoft notes.
ASA can come in handy to developers who can use it to test their apps for problems, to IT professionals for evaluating whether an app will be suited for use in their enterprise, to IT security auditors for evaluating the risk of an app during threat risk reviews, and to IT security incident responders, who can use it to gain a better understanding of the state of a systems security during investigations.
Microsoft welcomes contributions and suggestions for the tool and has set out a tentative roadmap for additional features it means to implement in ASA: live monitoring of network traffic and registry, scanning of drivers and firewall settings, and more.
Attack Surface Analyzer v.2.0 can be downloaded from GitHub.