Should you trust that Chrome extension? Use CRXcavator to decide
Duo Security has released CRXcavator, a tool that can help end users and enterprises make an informed decision about installing a specific Chrome extension.
About CRXcavator
CRXcavator was created as an internal tool by Duo’s Corporate Security Engineering team and, because it’s extremely helpful, they made it publicly available.
“CRXcavator automatically scans the entire Chrome Web Store every 3 hours and produces a quantified risk score for each Chrome Extension based on several factors,” the company explains.
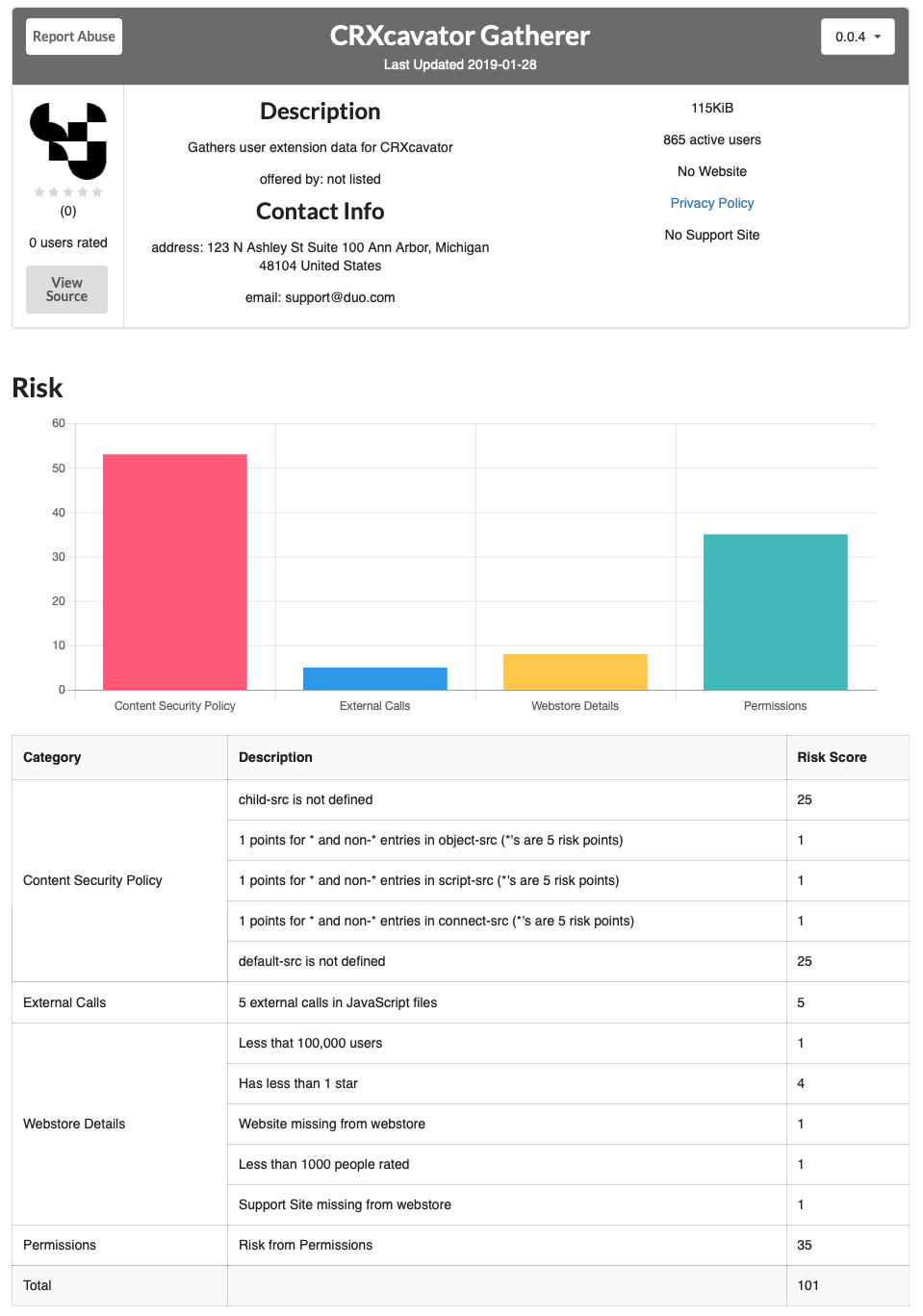
These factors include:
- Permissions
- Presence of potentially dangerous functions and possible entry points
- Inclusion of vulnerable third party Javascript libraries
- Weak (or non-existent) content security policies
- Missing details from the Chrome Web Store description
- Which sites the extension’s code likely makes external requests to, and more.
The provided score and report can be used by end users to decide whether they will install the extension and by organizations to set up a whitelist of extensions they will permit their employees to use. The tool also identifies related extensions as lower-risk alternatives for shady or risky extensions.
Finally, users can also choose to get notified via an RSS feed whether an extension they use has been changed and has potentially become malicious.
“Even if a security team has approved an extension, its functionality can change over time, often without notice,” Duo Security points out.
“One scenario where this applies is if a malicious third party were to gain control of the extension, perhaps by buying it from the developer or compromising the developer’s account. The third party could add malicious code and push the new version out to existing users without triggering another security review. Manually reviewing every update to extensions allowed in an organization’s domain is not feasible for most security teams.”
The company has also created the CRXcavator Gatherer Chrome extension, which help organizations gather Chrome Extension usage statistics across the enterprise.
A much needed solution for a long-standing problem
Even though Google is doing a lot to minimize the risk of bad extensions, risky extensions are far from rare.
Earlier this year Duo Security scanned 120,463 extensions and apps present in the Chrome Web Store, and found that:
- 35.4% could read user data on any site
- 31.8% use third-party libraries that contain publicly known vulnerabilities
- 15% has vulnerable third-party libraries and could read user data on any site
- 9% can read user cookies
- 84.7% don’t have a privacy policy listed
- 77.3% don’t have a support site listed.
“Of the 95k extensions in the Web Store that support Content Security Policies at the time of our analysis, we found that 74,403 (78.3 percent) do not have a CSP defined and, beyond that, 94,059 extensions (99 percent) do not have default-src or connect-src in the CSP defined. These are the parts of the CSP that give developers the ability to restrict which external resources the extensions can access and where the extensions can send the data they collect,” the company noted.
“CRXcavator fills the gap between what Google deems safe enough for distribution via the Web Store, and what users or businesses deem safe for their own use based on their own individual risk preferences.”