Biotech platforms keep missing the mark on security fundamentals
A new security posture report on the biotech sector shows how quickly attackers could reach sensitive health data with only basic reconnaissance. Researchers needed less than two hours per company to uncover exposed genomic records, unprotected APIs, and misconfigured systems, according to Sekurno.
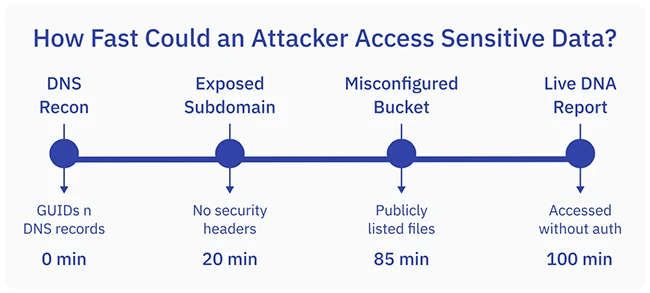
Real-world timeline showing how attackers could pivot from passive reconnaissance to accessing sensitive genomic data in under 2 hours.
APIs exposing sensitive data
APIs were the most common weakness, accounting for 34% of identified issues. In several cases, endpoints exposed personal information, such as patient IDs, genetic reports, and partner data, without requiring authentication. Some platforms also left developer documentation, including Swagger and GraphQL introspection, publicly accessible, successfully mapping the entire API surface. These conditions allowed unauthorized requests to succeed against endpoints that appeared secure.
Internal system details leaking out
More than half of the companies revealed internal details through verbose error messages, exposed configuration files, or non-minified JavaScript. These disclosures included usernames, user IDs, file paths, and backend framework information.
In some cases, hardcoded secrets like API keys or private tokens were visible in frontend code. Verbose errors also revealed stack traces and server internals. Together, these leaks lowered the effort required to map systems and identify exploitable weaknesses.
Corporate credentials easily found
Around 36% of companies had corporate credentials discoverable through public sources. Many were email-password pairs linked to company domains, with some firms having 15 or more exposed combinations. These leaks originated from prior third-party breaches and stealer logs, pointing to widespread credential reuse. Even without testing their validity, the presence of these credentials demonstrated how easily attackers could attempt credential stuffing or account takeovers.
Vulnerable, outdated software
A number of companies were running outdated software with known vulnerabilities. This included unpatched versions of Apache HTTP Server and PHP, affected by multiple CVEs that could enable remote code execution or information disclosure. Some platforms also used vulnerable third-party libraries.
The persistence of these outdated systems often pointed to gaps in asset inventory and the absence of structured vulnerability management, leaving internet-facing services exposed to automated scanning and exploitation.
Publicly accessible development environments
Several companies had staging or development environments exposed to the public. These often reused production logic or credentials and lacked proper access controls. Examples included open Kubernetes dashboards, default Apache pages, and publicly accessible databases. In some cases, the only safeguards were static credentials or basic form logins. These environments served as entry points that attackers could locate and exploit, sometimes with the same level of access as production systems.
The risk landscape
For companies handling genomic data and health records, these gaps represent both operational and reputational risk. The report warns that violations of HIPAA or GDPR are possibilities. Breaches could also shake investor confidence in a sector where trust is foundational to the adoption of personalized medicine.
The report points to the 23andMe incident as a case in which overlooked controls, such as MFA or consent defaults, amplified the impact of a breach. Although the researchers did not attempt exploitation, the timeline presented shows how an attacker could move from passive reconnaissance to accessing live DNA reports in less than two hours.
“We didn’t spend more than two hours per company, and yet weidentified expose d DNA data, multiple misconfigurations, weak (or even absent) authentication, exposed client databases, and more. We find this extremely concerning, as trust is fundamental to the evolution of this industry, and our findings show that this trust can be easily undermined”, said Demyd Maiornykov, CEO, Sekurno.