Network Flight Simulator: Open-source adversary simulation tool
Network Flight Simulator is a lightweight utility that generates malicious network traffic and helps security teams evaluate security controls and network visibility.
The tool performs tests to simulate DNS tunneling, DGA traffic, requests to known active C2 destinations, and other suspicious traffic patterns.
“There’s so much snake oil within the security industry regarding threat detection coverage in products across the board (e.g., EDR, SIEM, firewalls, proxies) that leads to security teams making uniformed purchasing decisions. We see this at AlphaSOC when we generate alerts based on C2 and exfiltration activity, which don’t trigger from other tools within customer environments. We created Network Flight Simulator to enable teams to quantify and measure the coverage of their existing tools and detections,” Chris McNab, co-founder of AlphaSOC, the company behind Network Flight Simulator, told Help Net Security.
AlphaSOC track malicious infrastructure across malware families and C2 frameworks (e.g., Cobalt Strike, Mythic, Metasploit) and Network Flight Simulator uses this live data to synthesize traffic to current malicious infrastructure online. The tool isn’t using a static list of destinations to test but retrieves live C2 destinations from the AlphaSOC API.
The system also generates traffic to live “lookalike” domains that we have registered to impersonate known brands online so that teams can evaluate coverage about spear phishing and targeted attack patterns (e.g., those used by Lazarus Group in recent months).
The modules packaged with the utility are:
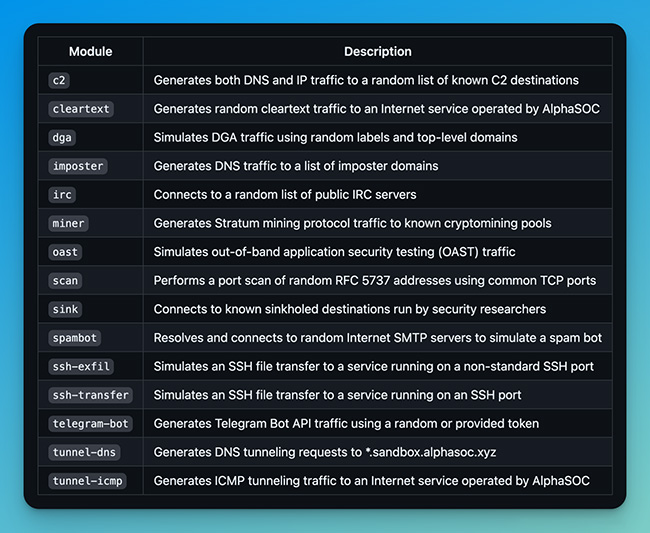
“Being an open-source project hosted on GitHub, we have new modules proposed that extend coverage to exfiltration patterns over SCTP, FTP, encrypted DNS, Tor, and mail channels (e.g., POP3 and SMTP as used by many malware families). These are malicious patterns that legacy security products and SIEM platforms have challenges in identifying, and we’d like to help security teams better understand and plug the gaps in their detection coverage,” McNab concluded.