Federal agencies gear up for zero trust executive order deadline
Federal agencies are prepared to meet the zero trust executive order requirements from the Biden Administration with just over a year until the deadline, according to Swimlane.
The research investigated the confidence level of these agencies in meeting the memorandum’s requirements and the tools leveraged to overcome challenges in adopting the key components of a zero trust architecture.
“As a country, we are confronted with a multitude of unprecedented cybersecurity challenges that have put cybersecurity front and center in the federal government,” said James Brear, CEO of Swimlane.
“It’s more critical than ever that the public sector is empowered by the right solutions that will keep our country protected while staying on top of regulatory compliance. This research should serve as a starting point for conversations around how technology can enable security teams to respond swiftly to incidents to safeguard national interests and public trust,” Brear continued.
Security automation is a necessity. Are Federal agencies ready?
67% of government agencies are confident or very confident they are prepared to meet the zero trust requirements laid out by the U.S. government’s Memorandum M-22-09, which includes implementing security orchestration, automation, and response (SOAR) technology.
When asked how agencies are arming themselves with the tools needed to meet all the criteria of implementing a zero trust architecture and solve the sophisticated security challenges, 64% of federal agencies said they are choosing low-code security automation.
The need for security automation to address government agencies’ pain points is not a new concept, but Memorandum M-22-09 has shined a spotlight on its importance. According to the recently published Forrester Tech Tide: Zero Trust Threat Detection And Response report, “SOAR tools help security teams orchestrate response processes and automate response actions. When properly managed, this can remove manual and repetitive work performed by security analysts for investigation and response. SOAR can also be used for metrics gathering and incident case management. Ultimately, SOAR acts as middleware to facilitate communication and action between security tools that would otherwise not be able to interact.”
Grappling with security team vacancies
Today’s security teams within the federal government are expected to investigate and remediate thousands of alerts daily while keeping up with evolving mandates.
- 83% of federal agencies report having security team positions currently open.
- 64% of federal agencies report it takes longer to fill a security position now than it did two years ago.
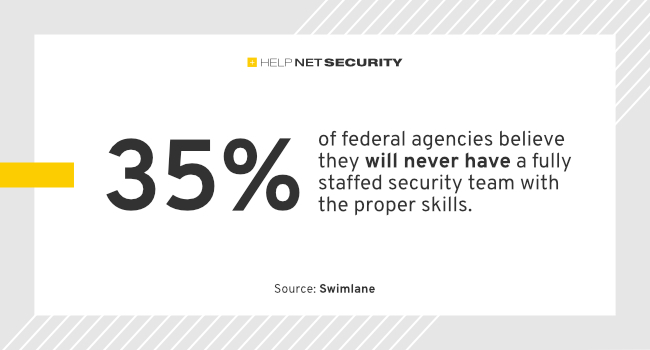
- 35% of federal agencies believe they will never have a fully staffed security team with the proper skills.
Turning to optimal technology
Federal agencies are turning to low-code security automation to lighten the load of implementing the SOAR component of the executive order. 99% of agencies cited benefits to low-code automation platforms, including the ability to address all security automation requirements while relying less on coding skills. These advantages are key for smaller security teams that may not have the required skill set to implement a traditional SOAR solution.
On the other hand, more than nine-out-of-10 federal agencies are finding that no-code solutions do not support cloud or hybrid environments and lack important reporting and case management features. More importantly, federal agencies cited that no-code automation tools are only short-term solutions to long-term issues.
“Working in IT and security roles at the Department of Homeland Security (DHS) and the U.S. Defense Information Systems Agency (DISA), I have witnessed firsthand the hurdles security practitioners face in the public sector,” said Cody Cornell, chief strategy officer of Swimlane.
“Without the right security tools, there is simply no way for federal agencies to handle the volume of security alerts their teams are confronted with today. It’s encouraging to see that federal agencies understand what they’re up against and that talent alone won’t address evolving cybersecurity challenges,” Cornell concluded.