Phishing campaign targets ChatGPT users
A clever phishing campaign aimed at stealing users’ business email account credentials by impersonating OpenAI, the company behind the ChatGPT chatbot, has been spotted by Inky researchers.
The attack
ChatGPT has quickly gained popularity and is used widely by individuals and organizations. That’s enough of a reason for cybercriminals to impersonate the brand.
The initial phase of the attack involves the victim receiving an email that appears legitimate, purportedly sent by OpenAI. The email requests the recipient to verify their email address in order to continue using their ChatGPT account setup. To further deceive the victim, the threat actors manipulate the sender’s domain to make it seem as if the email originated from their organization’s IT support.
Within the email, a “verify your email” button is provided, containing a malicious link. Upon clicking the link, the victim is redirected to a deceptive website designed to resemble their organization’s legitimate site. Here, they are prompted to enter their login credentials.
Although the first login attempt returns an error message, the victim’s sensitive data has already been captured by the attackers. Subsequently, a second login attempt redirects the victim to their own domain (i.e., the organization’s legitimate domain).
“The redirection happens because the personal code uses a my_slice variable “window.location.replace()” to construct a new URL (…) and replace the existing malicious URL,” INKY experts explained.
“As an extra benefit to the phishers, when they used replace(), the phishing site was not saved in the browser’s session history. So, the recipient would not be able to use the back button to navigate back to the phishing site.”
Clever tactics
The link pointing to the phishing page is crafted so that it automatically creates a convincing phishing page based on the domain name in the victim’s email address.
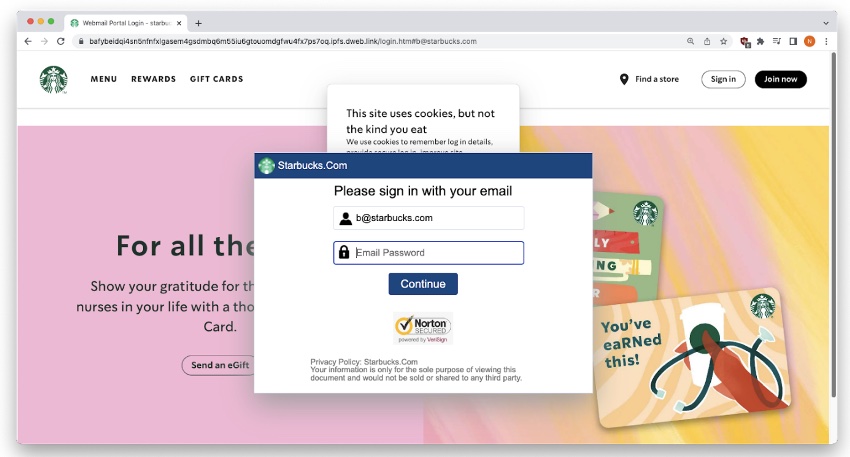
Malicious site impersonating the victim’s domain (Source: INKY)
The attackers are also using the InterPlanetary File System (IPFS) – a distributed file storage protocol that enables computers to store and share files within a vast peer-to-peer network – to host the phishing page, to make it more resilient to takedown.
“IPFS peer-to-peer model is distributed and hosted amongst multiple nodes in the network. These attacks are resilient to takedowns because the phishing content exists on multiple nodes at the same time so phishing content is still active even if one node is targeted,” they explained.