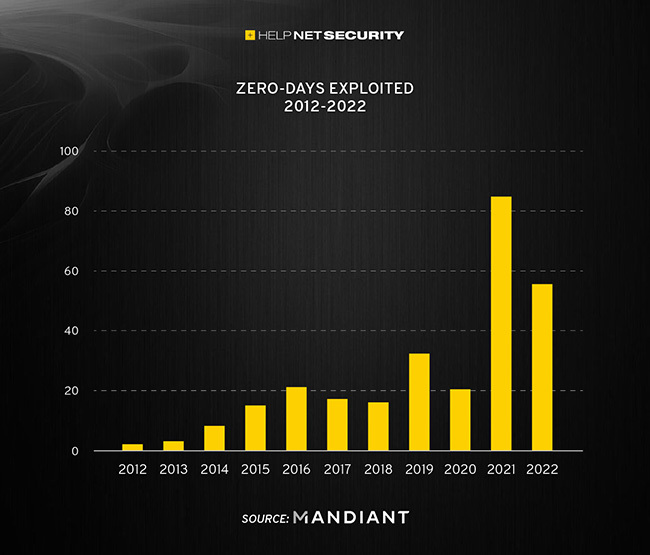
2022 witnessed a drop in exploited zero-days
Malicious threat actors have actively exploited 55 zero-days in 2022 – down from 81 in 2021 – with Microsoft, Google, and Apple products being most targeted.
53 out of 55 allowed attackers to achieve elevated privileges or execute remote code on vulnerable devices, a new Mandiant report has revealed.
“While information disclosure vulnerabilities can often gain attention due to customer and user data being at risk of disclosure and misuse, the extent of attacker actions from these vulnerabilities is often limited. Alternatively, elevated privileges and code execution can lead to lateral movement across networks, causing effects beyond the initial access vector,” the company’s analysts noted.
N-day vulnerability exploitation
Thirteen zero-day vulnerabilities were exploited by cyber espionage groups, with Chinese state-sponsored actors exploiting seven of those, and North Korean attackers two. Four zero-days have been attributed to financially motivated threat actors, three of which have been linked to ransomware operations.
Although the exploitation of zero-day vulnerabilities by financially motivated threat actors decreased in 2022, Mandiant found that n-day vulnerability exploitation – which involves exploiting vulnerabilities that have already been patched – was still commonly used as an initial infection vector in ransomware and extortion incidents.
The distribution of technologies affected by zero-day vulnerabilities remained similar to previous years, with the three largest vendors whose technology is widely adopted across the world being the primary targets:

Popular technologies are the most desirable targets
Additionally, the products most frequently exploited through zero-day vulnerabilities were:
- Operating systems (19)
- Browsers (11)
- Security, IT, and network management products (10)
- Mobile operating systems (6)
Windows was the OS most often targeted for exploitation (15 zero-days), while macOS zero-days exploited in 2022 were only four.
Chrome was the primary target for browser exploitation, with nine out of 11 browser zero-day vulnerabilities.
Threat actors often target security, network, and IT management products, as well, as they are always exposed to the internet and typically don’t have EDR/XDR or other detection solutions to protect them.
“These devices are attractive targets for multiple reasons. First, they are accessible to the internet, and if the attacker has an exploit, they can gain access to a network without requiring any victim interaction. This allows the attacker to control the timing of the operation and can decrease the chances of detection. Malware running on an internet-connected device can also enable lateral movement further into a network and enable command and control by tunneling commands in and data out of a network,” the analysts pointed out.
“It is important to note that many of these types of products do not offer a simple mechanism to view which processes are running on the device’s operating systems. These products are often intended to inspect network traffic, searching for anomalies as well as signs of malicious behavior, but they are often not inherently protected themselves.”
The importance of speedy patching
Mark Lamb, CEO of HighGround.io, says that these findings aren’t very surprising given that unpatched zero-days provide a guaranteed way for attackers to infiltrate organizations.
“What is surprising is how much zero-day exploitation has gone down since 2021,” he added. “Businesses should use this data to reinforce the importance of patching, even if they can cause business disruptions. As soon as zero-days are disclosed, the clock starts ticking on attackers who are looking for ways to exploit them, so as soon as fixes are released, these must be prioritised and applied to systems. When it comes to patches, most large vendors release them on a specific date every month, so these should be applied as close to release as possible.”