Google ads increasingly pointing to malware
The FBI has recently warned the public about search engine ads pushing malware diguised as legitimate software – an old tactic that has lately resulted in too many malicious ads served to users searching for software, cracked software, drivers – anything that can be downloaded, really – via Google and Bing.
The recent explosion of search engine malvertising
Malware peddlers employ a variety of methods to deliver their wares to unsuspecting users:
- Malicious links or attachments served via email and messages, or posts on social media, online forums and IM groups
- Malicious ads served via popular sites
- SEO poisoned websites
- Malicious ads served by popular search engines
The latter tactic is particularly good at hitting a wide pool of potential targets, since most internet users also use search engines.
Lately, though, they have been overdoing it – or perhaps it’s just that more people have begun noticing it and talking about it online?
Many documented campaigns
HP threat researcher Patrick Schläpfer says that they have seen “a significant increase in malware distributed through malvertising, with multiple threat actors currently using this technique.”
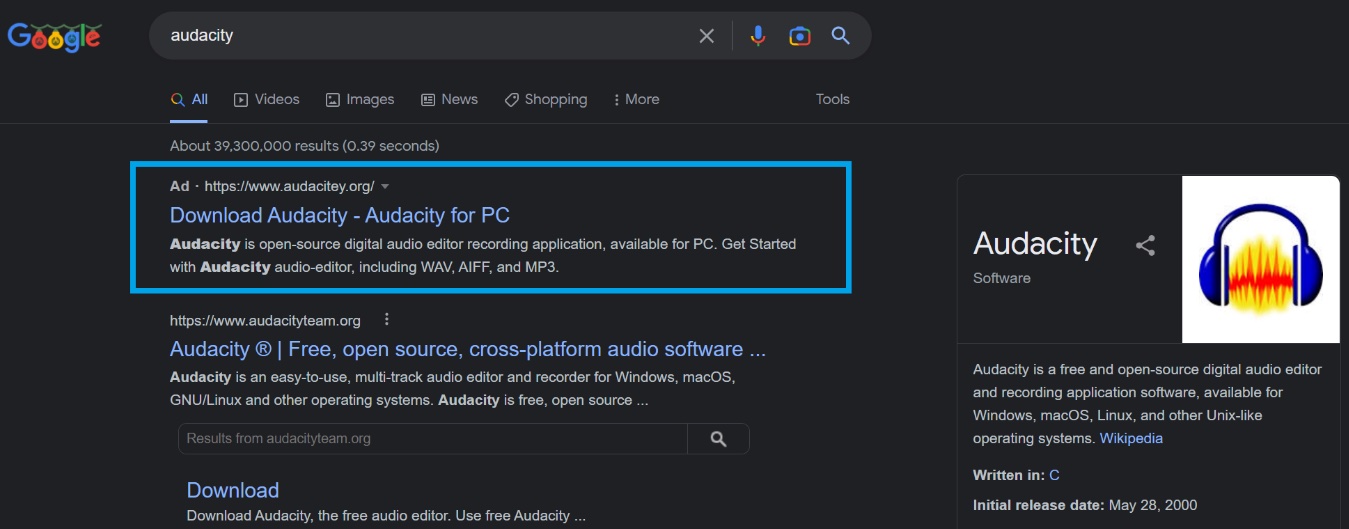
Some of these campaigns have been going on since late last year, and mostly target users searching to download popular software (e.g., Audacity, Blender 3D, GIMP, Notepad++, Microsoft Teams, Discord, Microsoft OneNote, 7zip, OBS, etc.).
The malicious ads often manage to be the first link users see when searching for software on Google, and point to a (usually typosquatting) domain that resembles the original software manufacturer’s page. Clicking on the download link triggers the download of the malicious package from a file-hosting and sharing service (e.g., Dropbox), an app development platform (e.g., Google Firebase), or a code-hosting service (e.g., GitHub).
Protect yourself and your loved ones
While Google and Microsoft are trying to keep their users safe, it’s becoming obvious that they are failing to keep pace with the rapid change of tricks employed by cybercriminals to push those ads.
As some ads are removed and new ones inevitably spring up, we are forced to do what we can to protect themselves.
Just being aware of this danger and knowing about the prevalence of these malicious ads will help. Also, carefully check whether the URL to which the advertisement points is the correct one (e.g., by comparing it with the official domain listed on the software’s Wikipedia page).
If you fail to spot the malicious nature of the ad and the typosquatting site, don’t ignore warnings you might get from Microsoft Defender or another security solution you use.
But the best advice may be to completely avoid clicking on Google and Bing ads – either by recognizing them and avoiding them consciously, or by installing an ad-blocking extension that will stop those ads from being displayed. That latter option is perhaps the best one for less tech-savvy users, to completely remove the temptation of willy-nilly clicking on potentially malicious ads – wherever they might pop up.
Google and Microsoft, on the other hand, may want to ramp up their efforts to block this kind of abuse of their ad network, or risk their reputation being dented and more and more users start using ad blockers.