Infosec products of the month: October 2022
Here’s a look at the most interesting products from the past month, featuring releases from: ABBYY, ARMO, Array, AuditBoard, AwareGO, Code42, Corelight, Digi International, EnigmaSoft, Exabeam, HashiCorp, Illusive, Kasten by Veeam, Legit Security, LiveAction, LogRhythm, Mandiant, Pentest People, Portnox, Prove, RSA, SkyKick, Socure, Stytch, Thales, and Verica.


AuditBoard ESG enables users to centralize and manage their ESG programs
AuditBoard ESG centralizes data in a single system of record; simplifying evidence collection and reporting; and enabling teams to perform materiality assessments. The integrated solution also aligns topics and metrics against common reporting frameworks — including the Sustainability Accounting Standards Board (SASB), the Global Reporting Initiative (GRI), and the Task Force on Climate-Related Financial Disclosures (TCFD) — to identify gaps and surface overlapping requirements.


Pentest People SecurePortal 2.0 enables users to identify vulnerabilities as they appear
Pentest People re-engineered its SecurePortal product to provide customers with continuous, cloud-based vulnerability monitoring and penetration testing as a service (PTaaS). Its intuitive dashboard shows when vulnerabilities first emerged, their level of severity, and when they were addressed, allowing organizations to track their security posture over the course of the year.


LogRhythm Axon helps SecOps manage data and operational infrastructure
LogRhythm has unveiled LogRhythm Axon, a cloud-native security operations platform built for security teams that are stretched thin by overwhelming amounts of data and an ever-evolving threat landscape. It reduces the burden of managing data and the operating infrastructure, helping security teams prioritize and focus on the work that matters.


Verica ProwlerPro SaaS strenghtens security posture for companies running software on AWS
Verica launched ProwlerPro SaaS, providing companies running software on AWS with free AWS security solution. Once an account is created, the service can run over 250 checks on a user’s AWS account in minutes. When an incident occurs, organizations no longer must worry about clunky back-end software or multiple roadblocks through a vendor to diagnose the solution.


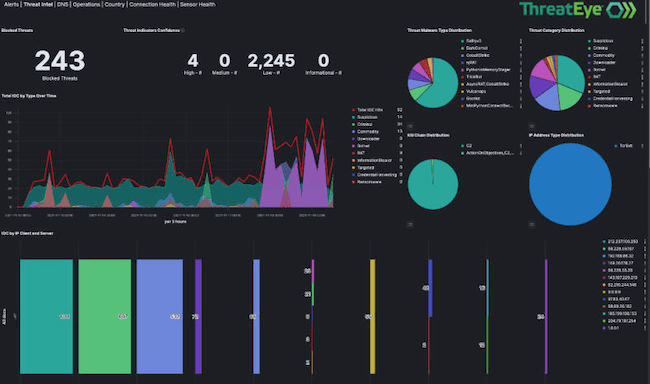
LiveAction enhances ThreatEye to help security teams identify behavior in encrypted traffic streams
LiveAction has released the next generation of ThreatEye, the company’s NDR platform. It includes a new User Interface (UI) to deliver simplified management of the threat investigation lifecycle, allowing SOC analysts to correlate sets of findings and policy violations to track the state of incidents, delivering enhanced workflow capabilities that speed threat identification and remediation.

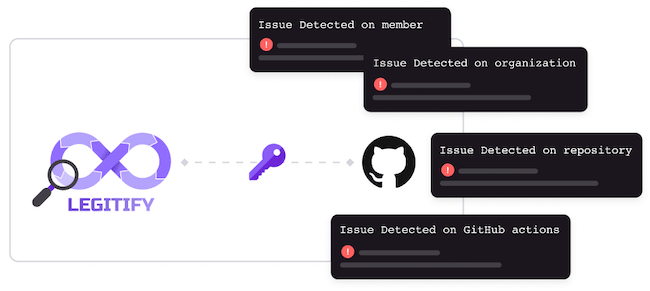
Legit Security Legitify detects security and compliance issues across GitHub assets
Legitify connects to GitHub via an access token and detects issues across four resource types: member, repository, actions, and organization. It provides the option to scan by specific GitHub instance and/or resource type, or to scan an entire GitHub organization across all resource types.

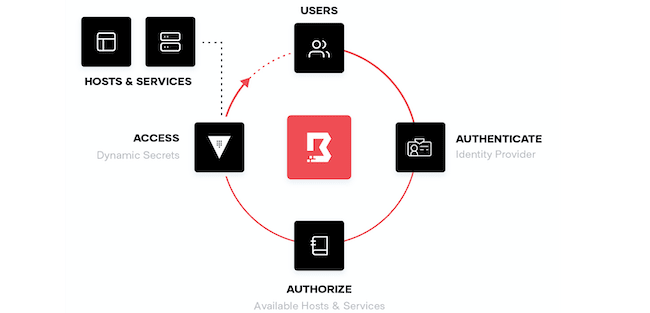
HashiCorp HCP Boundary helps organizations struggling with security as they transition to the cloud
HCP Boundary allows teams and users to access the critical systems they need while abstracting the session connection, establishment, credential issuance, and revocation. Boundary provides operations and security teams the ability to pull in cloud service catalogs and on-premises resources and map out policies to which systems, users, and groups should have access.

Digi SAFE: Connectivity solution for public safety and transportation agencies
The Digi SAFE connectivity solution is purpose-built, secure, and suited for widespread deployment by emergency services organizations of all sizes and budgets. At its core, Digi SAFE features Digi Remote Manager as the command center of an intelligent public-safety network that enables IT support teams to remotely monitor, manage, and update field devices.


Portnox introduces IoT fingerprinting and profiling solution to address rising IoT security threats
Portnox’s new IoT fingerprinting and profiling capabilities empower organizations to identify, authenticate, authorize, and segment IoT devices across their network to ensure an effective zero trust security posture. This technology will unlock a tremendous number of additional capabilities, such as automatic policy mapping based on fingerprints and leveraging fingerprinting data to thwart potential MAC Address spoofing risks.


Thales improves digital sovereignty requirements across public service clouds
Thales announced the latest innovations of CipherTrust Cloud Key Manager that help organizations address digital sovereignty requirements across major public clouds. Organisations that leverage these cloud providers can now leverage CipherTrust Cloud Key Manager’s Bring Your Own Key (BYOK) capabilities for enhanced data security and encryption key ownership.


Stytch Strong CAPTCHA protects users from bots and CAPTCHA farms
Stytch unveils Strong CAPTCHA to help users reduce online fraud and risk. The solution enables businesses to interact with legitimate customers and also cuts costs for businesses in the form of fraud, wasted resources, and time.


ABBYY Proof of Identity simplifies document-centric digital onboarding
ABBYY Proof of Identity combines document-centric identify proofing and identify affirmation into a single solution. It assures that the ID is valid, authentic, and that the applicant is who they say they are, and affirms this via supporting documentation.

Code42 enhances Incydr Risk Indicators to help users protect and classify sensitive data
Code42 has enhanced its Incydr Risk Indicators (IRIs) within the Code42 Incydr product to detect and label file downloads from corporate systems. By understanding the source system from which a file came, security analysts can better prioritize what data exfiltration presents the most risk to their organization.


RSA Mobile Lock detects critical threats on mobile devices
By constantly scanning for high-risk security threats, RSA Mobile Lock can help establish device trust. Whenever it detects critical threats, Mobile Lock can prevent users from authenticating into a secured environment until the threat is resolved while simultaneously alerting IT admins about the issue.


Exabeam New-Scale SIEM enables security teams to defend against complex threats
New-Scale SIEM is a combination of cloud-scale security log management, behavioral analytics, and an automated investigation experience. Built on the cloud-native Exabeam Security Operations Platform, the New-Scale SIEM product portfolio gives worldwide security teams better fighting chance at defeating adversaries with advanced threat detection, investigation, and response (TDIR).


Mandiant Breach Analytics empowers enterprises to gain insight on breach activity in IT environments
Mandiant Breach Analytics is designed to enable organizations to reduce attacker dwell time by continuously monitoring events in Chronicle for current, relevant indicators of compromise and applying contextual information and machine learning to prioritize the matches. With active insight into threats, organizations can take action to mitigate the impact of targeted attacks, while reducing the cost of current approaches.


AwareGO Employee Cybersecurity Risk Audit identifies weak points associated with human risk
AwareGO launched full Employee Cybersecurity Risk Audit and consultation to help organizations identify critical cybersecurity risks among employees. In this audit, cybersecurity experts work directly with individual organizations to set up the appropriate assessment, execute it, evaluate the outcome and map that to effective risk-reducing decisions.


EnigmaSoft SpyHunter Pro combines anti-malware detection and blocking to enhance privacy protection
SpyHunter Pro is a Windows anti-malware application that combines SpyHunter’s system guards to help block malware before they cause damage, plus anti-malware detection and removal algorithms, along with new premium features, including functionality purposely designed to enhance privacy protection and optimize computers.


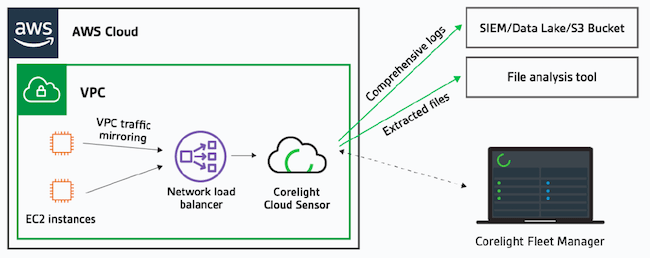
Corelight Cloud Sensor SaaS for AWS accelerates incident response for security teams
With Corelight Cloud Sensor SaaS for AWS, security teams can achieve uniform network visibility for incident response and threat hunting capabilities to cloud environments without the burden of having to set up and manage the monitoring infrastructure themselves.

ARMO adds CIS benchmark to Kubescape to help users scan Kubernetes and CI/CD pipelines
ARMO announced that Kubescape now includes security and compliance scanning of Kuberneters based on the CIS Kubernetes benchmark. Kubescape calculates risk scores based on the CIS Kubernetes framework and tracks them over time to show how organizations are improving their security posture or drift from standards.


Socure releases Sigma Synthetic Fraud Model to identify manipulated and fabricated identities
Sigma Synthetic Fraud combines the knowledge and experience of expert fraud investigators with the computational and statistical capabilities of advanced ML to mitigate rapidly evolving and complex synthetic patterns. Additional enhancements include new sources of credit header and inquiry data, which when combined with existing data sources and internal velocity data, helps with risk signaling and identifying anomalous synthetic patterns.


SkyKick Security Manager enables ITSPs to manage Microsoft 365 security
Security Manager is purpose-built for for information technology services providers (ITSPs) to find, fix and automate security across thousands of potential security issues for Microsoft 365 services. It transforms millions of security signals into actionable insights through a single pane of glass.


Illusive’s ITDR solution discovers and remediates identity vulnerabilities
Illusive’s ITDR solution, Illusive Spotlight and Illusive Shadow, enables the comprehensive discovery of the unmanaged, misconfigured and exposed identity risks that leave every organization vulnerable to attack. It delivers aggregated, prioritized and contextualized insights into identity risks, so that security teams can focus on responding to their greatest risks first.


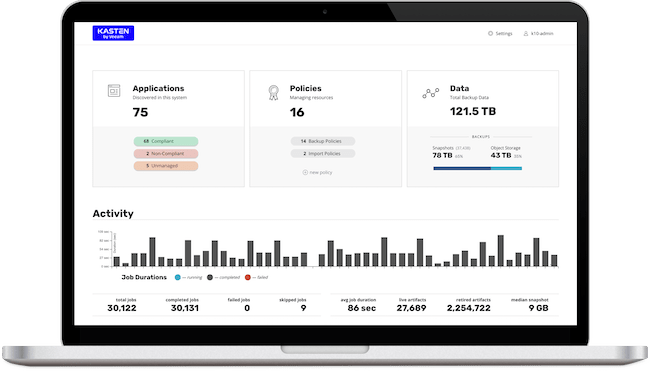
Kasten K10 v5.5 simplifies Kubernetes data protection for operations teams
Kasten by Veeam has released the new Kasten by Veeam K10 v5.5 Kubernetes data management platform. As a complement to the suite of modern data protection and recovery solutions offered by Veeam to protect all data assets across virtual, cloud-native, SaaS, Kubernetes and physical workloads, these advancements will address the challenges historically found in Kubernetes around operational complexity at scale.

HelloPrivacy by Array helps customers improve their online privacy
HelloPrivacy by Array introduced a suite of embeddable consumer digital privacy products that companies of all sizes and industries can offer customers to help them clean up, protect, and improve their online privacy by finding and removing their personal information from the web.


Prove Auth empowers companies to reduce reliance on passwords and one-time passcodes
Prove Auth enables companies to reduce reliance on passwords and one-time passcodes (OTPs) and empowers consumers to frictionlessly authenticate in all channels including phones, desktops and call centers. It also protects consumers from fraud including account takeovers.

