Microsoft makes tamper protection for macOS endpoints widely available
The tamper protection feature in Microsoft Defender for Endpoint for macOS is getting rolled out to all customers, the company has announced on Monday.
The feature is meant to:
- Protect the endpoint security solution/agent from being uninstalled or its activity stopped by attackers
- Prevent the editing, deletion, and renaming of existing Defender for Endpoint files, as well as the creation of new files under Defender for Endpoint location.
But those protections are active only if the solution is put in “Block” mode, and Microsoft is rolling out the feature in “Audit” mode by default, so admins can “get a sense of how the feature detects actions that are indicative of tampering attempts.”
In Audit mode, the solution logs (but does not block) all of the aforementioned actions – except commands to stop the agent.
Audit before Block mode
“While in Audit mode, TP [tamper protection] signals can be viewed via Advanced Hunting and in local on-device logs. No tampering alerts are raised in the Security Center while in Audit mode. Alerts are raised in the portal only in block mode,” explained Camilla Sophie Djamalov, a Program Manager Intern at Microsoft.
The company has also shared an Advanced Hunting query to help admins observe tampering events in the Microsoft 365 Defender portal.
“Later this year, we will offer a gradual rollout mechanism that will automatically switch endpoints to Block mode; note this will only apply if you have not specifically made a choice to either enable (Block mode) or disable the capability,” Djamalov added.
Enabling tamper protection on Microsoft Defender for Endpoint on macOS devices
Microsoft Defender for Endpoint is an enterprise endpoint security platform aimed at preventing, detecting, investigating, and responding to advanced threats targeting enterprise networks.
The tamper protection on macOS is supported for macOS Monterey (12), Big Sur (11), and Catalina (10.15+), and the minimum required version for Defender for Endpoint is v101.70.19.
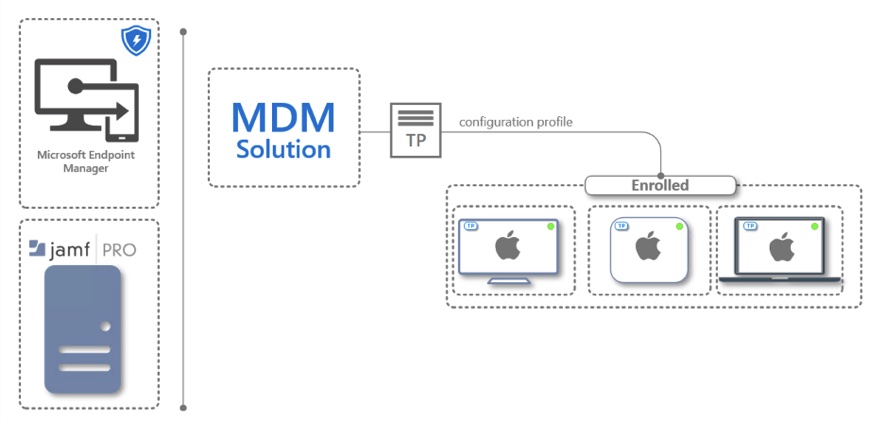
Use an MDM solution to enable tamper protection on various macOS devices (Image credit: Mohamed ElKhouly)
Microsoft also advises enabling System Integrity Protection (SIP) and using a Mobile device management (MDM) tool such as Microsoft Endpoint Manager (formerly Intune) or JAMF Pro to configure Microsoft Defender for Endpoint on macOS devices.
For more information, admins should check out Microsoft’s documentation.