New infosec products of the week: June 10, 2022
Here’s a look at the most interesting products from the past week, featuring releases from Acronis, Code42, Cynet, Elastic, Living Security, Lumu, NetWitness, Qualys, SafeBreach, and Swimlane.


Acronis Advanced DLP protects businesses and MSPs from data leakage
The integration of behavioral-based DLP capabilities into the Acronis Cyber Protect Cloud platform is what extends its ability to deliver unified data protection, cybersecurity and management across systems, data and workloads regardless of their location.


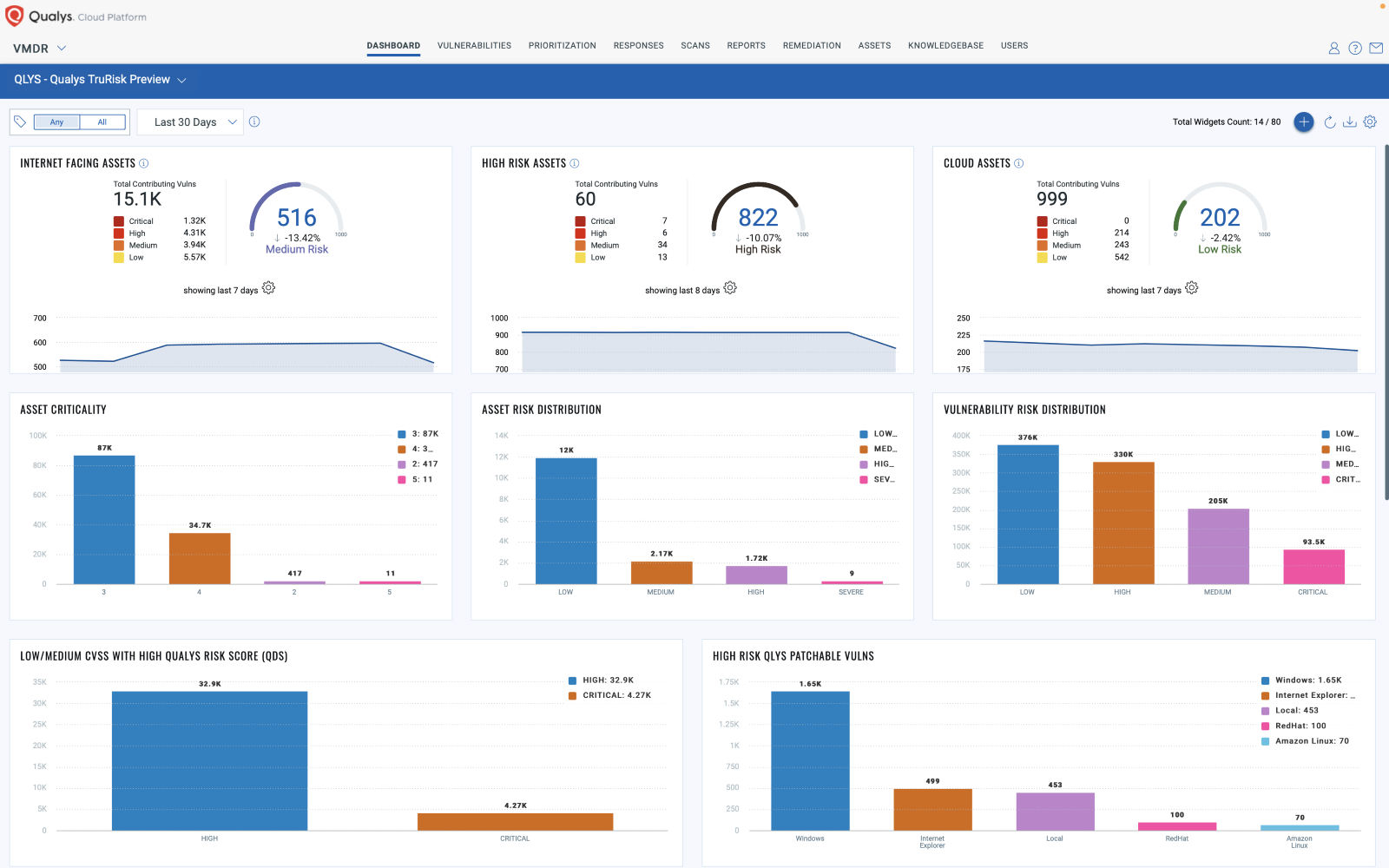
Qualys VMDR 2.0 provides security teams with insights into an organization’s risk posture
Qualys VMDR 2.0 helps security and IT teams increase efficiency and save time by providing shared context and the ability to create drag and drop workflows to automate time-consuming vulnerability management operational processes including vulnerability assessment of ephemeral cloud assets, alerting, and prioritization.

Cynet Automated Response Playbooks empowers security teams to reduce their alert investigation
Cynet’s Automated Response Playbooks automate manual tasks and workflows, empowering security teams to reduce their alert investigation and response times by 90%. In addition to freeing up valuable time for security teams, the playbooks provide a defined, consistent response process for more accurate security decisions and ensure that all alerts are properly addressed.


Code42 adds watchlists functionality to its Incydr product to help teams manage insider risk events
Code42 announced it expanded the data risk detection capabilities in the Code42 Incydr product to give security teams visibility and context to situational Insider Risk events. With Incydr’s watchlist functionality, security analysts can create user groups with common attributes from data that Incydr ingests, and automate investigation and response management workflows.


NetWitness XDR helps analysts detect known and unknown attacks
NetWitness XDR detects intrusions as they happen, using real-time visibility into network traffic across internal, internet-bound, virtual infrastructure and cloud computing environments, paired with deep, process-level endpoint visibility. Once an attack is detected, a prioritized and automated response enables an effective defense.


SafeBreach Studio enables security teams to automate and scale red-team exercises
SafeBreach announced SafeBreach Studio, a no-code red-team automation platform security teams of all skill levels can use to create, customize and execute sophisticated attack scenarios that replicate real-world adversary behavior.


Living Security Unify Insights allows organizations to identify human behavior risks
Unify Insights gives security leaders the ability to observe employees’ behaviors over time, identify those that present the most risk, and take targeted actions to address those threats, all while being able to measure and report on risk changes with other executives across the organization and with the Board.


Elastic Security for Cloud expands visibility and protection of cloud-native environments
Elastic Security for Cloud expands the capabilities of Elastic Security by bringing together the ability to enforce security posture for cloud-native and hybrid environments with infrastructure detection and response (IDR) to give customers deep visibility into cloud workloads and perform expert prevention, detection and response.


Swimlane Turbine extends visibility and response for security teams
Swimlane Turbine is a low-code security automation platform that captures hard-to-reach telemetry and expands actionability beyond the closed extended detection and response (XDR) ecosystem. Turbine analyzes incident data in real-time so that analysts can instantly execute an array of actions specific to the case.


Lumu Incident View empowers security teams to prioritize incidents based on the progression of attacks
Lumu’s Incident View shows operators everything they need to know in one place for precise response. Teams receive actionable information about who was impacted, when the incident took place and how best to respond before it escalates to a bigger problem.

