Attackers use Microsoft Teams as launchpad for malware
Hackers are starting to realize that Microsoft Teams is a great means of spreading tentacles throughout an organization’s systems; since the start of the year, Avanan has been seeing hackers increasingly dropping malware in Teams conversation.
“We’ve seen thousands of attacks per month across our userbase,” Jeremy Fuchs, Cybersecurity Research Analyst at Avanan, told Help Net Security.
Current attacks
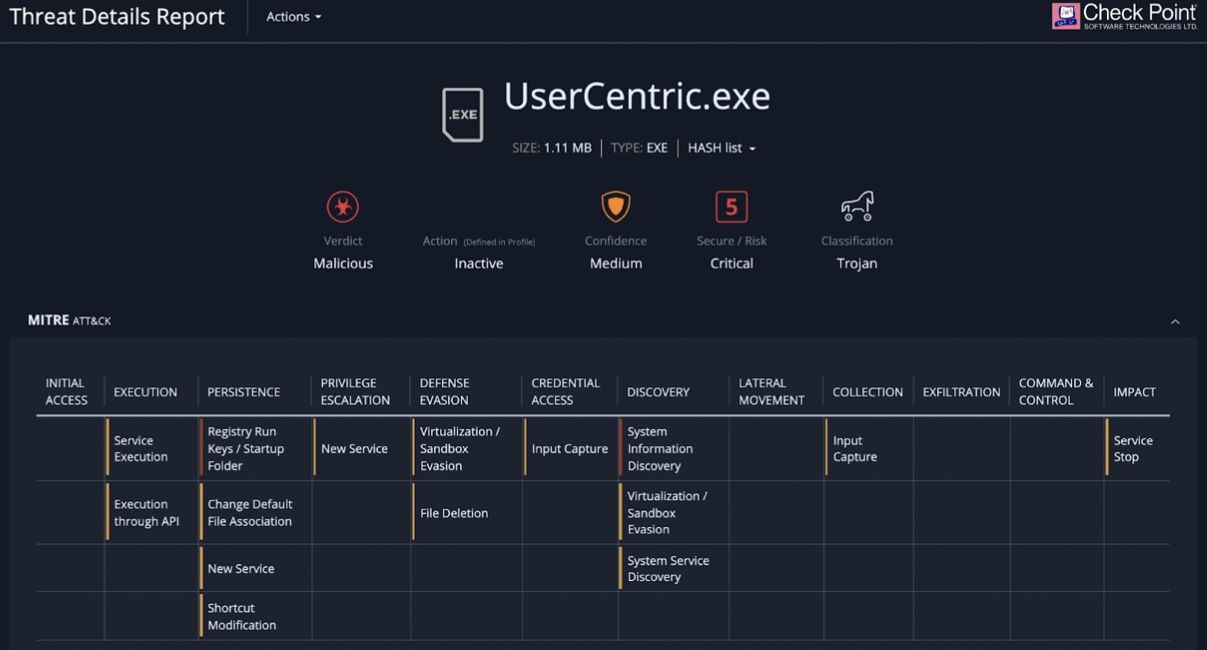
This iteration of this specific attack involves attackers attaching .exe files to Teams chats. The name of the file is currently UserCentric.exe, but that can be easily changed into another generic and innocuous-sounding label.
Once downloaded and run, the executable writes data to the Windows registry, installs DLL files, and creates shortcut links that allow the program to self-administer. In effect, it allows attackers to take control over the victim’s computer.
To be able to use this avenue of attack, hackers need to take control of a Microsoft Teams account. Since most professional Microsoft 365 editions include Teams, compromising Microsoft 365 credentials – either via phishing or by buying compromised credentials on the dark web – is the way to go about it.
Also, as Fuchs notes, attackers can compromise a partner organization and listen in on inter-organizational chats, or compromise an email address and use that to access Teams.
Microsoft Teams as the perfect means to spread malware
Many things make this type of attack possible. The malware apparently has virtualization/sandbox evasion capabilities. Scanning for malicious links and files is limited in Microsoft Teams, Fuchs says, and many third-party security solutions are not that great when it comes to Teams-specific protection.
In addition to this, while most employees have by now learned to second-guess identities in email, they still have an inherent trust in the identities on Teams.
“For example, an Avanan analysis of hospitals that use Teams found that doctors share patient medical information practically with no limits on the Teams platform. Medical staff generally know the security rules and risk of sharing information via email, but ignore those when it comes to Teams. In their mind, everything can be sent on Teams,” Fuchs explained.
“Further, nearly every user can invite people from other departments and there is often minimal oversight when invitations are sent or received from other companies. Because of the unfamiliarity with the Teams platform, many will just trust and approve the requests. Within an organization, a user can very easily pretend to be someone else, whether it’s the CEO, CFO or IT help desk.”