How can SMBs extend their SecOps capabilities without adding headcount?
Which is more important for achieving organizational cybersecurity: security products or security people? The right answer to this (trick) question is that both are equally important.
But while cybersecurity budgets are rising, most small and some midsize organizations looking to employ skilled cybersecurity professionals are often unable to match salaries offered by big enterprises in a job market where demand outstrips supply.
Outsourcing security: What’s on offer?
Fortunately, there is an alternative way for procuring security expertise: by retaining the services of managed security service providers (MSSPs) and managed detection and response (MDR) providers.
MSSPs usually assist organizations’ IT departments in managing the IT infrastructure and keeping it secure by managing security equipment/systems, monitoring security logs, supervising patch management, and similar preventative security measures. MDR providers concentrate on monitoring network traffic and data, providing threat hunting/detection services and responding to discovered threats – capabilities that are difficult for most SMBs to cultivate in-house due to resource limitations.
For example, when the existence of the Log4Shell vulnerability and a PoC for it was revealed, Milton Security, a California-based MDR provider, has been inundated with concerns and requests from customers, prospects, and the public asking to help make sense of the situation, provide credible and timely updates, and monitor networks for any suspicious activity that might be related to Log4j exploitation.
But they have also been getting a lot of requests for their application security testing, penetration testing, incident response, and even their vCISO service.
Choosing the right security service provider for your organization
If you have decided to retain the services of third-party cybersecurity experts, it’s important to ask and get satisfactory answers to numerous questions before taking the plunge.
“What types of devices and services can you monitor? What can you manage for me and what should I manage? How will we do this? Do you have to put devices in my network? Do you need to put agents on my endpoints? How do you scope the service? What does pricing look like? Is there a formal process to engage and onboard with you? How do you protect my data? Where will it be stored? Is my data going offshore? Who has access to my data? How do you protect your own systems? How do you let me know when there is a problem? What sort of reports am I going to get? How are we going to measure value?” James McMurry, CEO and Founder of Milton Security, recited the crucial questions to Help Net Security.
“Answers that should make you wary include: Measuring security value is ‘difficult’. We have a security alert framework (they are just sending you alerts of alerts that you already have). No clear answers to onboarding and service engagement. The MSSP should be very clear about how they protect data, what security control frameworks they use, and where it is stored. Vague answers here are a huge red flag.”
Milton Security’s 24x7x365 SOC
Also, not every service provider is a good fit for every type of organization. McMurry notes that, for example, tech-forward organizations with mature security teams have much less to gain from employing their services than an organization with a small security team that, while committed to security:
- Doesn’t know how to monitor for, detect, and respond to cybersecurity incidents
- Doesn’t have a SOC and doesn’t have the budget and capabilities to stand up one
- Doesn’t have the in-house expertise to come up with solid plans to improve their cybersecurity posture in the coming years.
Expert help from Milton Security
McMurry’s decades of experience in various companies in the cyber and network security arena made him realize a pattern in cybersecurity startups and the shortcomings they had, and he decided that he could do better.
“Cybersecurity startups were trying to be everything to everyone,” he noted. “My fear was that all those blinking lights and great ideas still did not help the small to midsize organizations out there that were at the greatest risk.”
So, in 2007, he started Milton Security with the goal to make cyber security affordable and within reach for all organizations. “We wanted to be a good fiscal steward for our customers while making sure they were protected,” he explained.
While the company started out with manufacturing their own network access control (NAC) devices and monitoring those devices for attacks, the customers wanted more: they started asking them to monitor their entire network. So they opened a security operations center and ultimately moved away from manufacturing and towards providing around-the-clock protection.
The company’s core services center on a combination of managed detection and response (MDR) and their proprietary extended detection and response (XDR), or as they refer to it, MxDR. This combination allows them to provide an AI/ML “sidekick” for their human threat hunters.
“We offer a true 24x7x365 security operations center (SOC), so our customers get the benefit of having actual humans watching over their networks as opposed to automated alerts outside of business hours. We also have a highly trained incident response team that is activated to assist with evaluating the threat, reducing exposure, remediating the attack, and mitigating future activity as soon as an incident is reported,” McMurry explains.
“Our AI/ML platform, Milton Argos Platform (MAP) was built with scalability and integration as a core focus. Combine that with threat intelligence from our 1MC-Labs team and hundreds of threat intelligence sources, data enrichment, and human analysis and you have a powerful alert and response solution that powers our Threat Hunters in their constant quest to keep your network safe.”
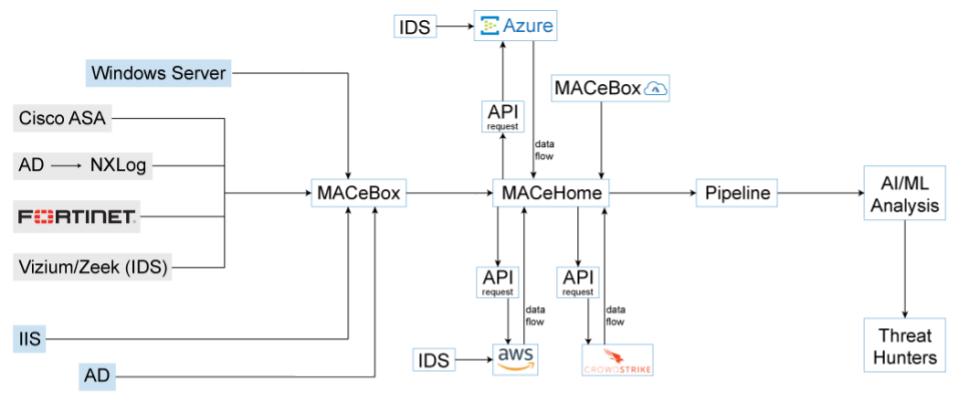
The data fueling their threat hunting efforts is collected via a lightweight virtual machine called MACe (Milton Argos Collection Engine), which can be adapted to collect data from any device that’s able to generate logs.
The data is collected from endpoints, on-prem and cloud systems and fed into the Argos Platform
On the offensive and preemptive side of things, Milton Security has recently also begun offering so-called expert services, which include penetration testing, network and application testing, network analysis, framework and security control assessments, and virtual CISOs that can advise customers and serve as a fractional security leader who reports to their board and provides thought leadership.
You don’t have to choose between security tools and people
In the 14+ years that Milton Security has been in the security business, they have seen many organizations feel forced to decide which is more important, security products or security people.
“Budget is usually the deciding factor between purchasing a security product that will spit out alerts that their IT and cyber team has to prioritize and address because they don’t have the budget to staff a fully operational SOC, or they do staff a SOC and everything has to be done manually,” McMurry says, and points out that they can provide both within an organization’s budget requirements.
“Because every organization has different security and compliance requirements, business processes, and so on, we create unique threat hunting and monitoring solutions and services to specifically cater to each customer. And because we’ve been hyper-focused on threat hunting and building the tools we need that provide support to our SOC and our customers, we’re really good at it and have been able to keep prices well within reach for our customers.”