Vulnerabilities in Nucleus NET TCP/IP stack could lead to real-world damage
Researchers have unearthed 13 vulnerabilities affecting the Nucleus NET TCP/IP stack and have demonstrated how attackers could exploit them to cause serious real-world damage.
The good news is that Siemens – the current owner of the stack – has released patches for all the vulnerabilities. The bad new is that it may take a while for these patches to be propagated downstream, i.e., for the patched Nucleus NET versions to be included in the various devices that use it.
About Nucleus NET
“Nucleus NET is the TCP/IP stack of the Nucleus Real-time Operating System (RTOS). The stack and the RTOS were originally developed by Accelerated Technology, Inc. (ATI) in 1993, then acquired by Mentor Graphics in 2002 and finally by Siemens in 2017,” Forescout and Mediagate Labs researchers explained.
The RTOS is apparently in use in more than 3 billion devices, most of which are device components (e.g., MediaTek IoT chipsets, baseband processors in smartphones and other wireless devices), but they are also used in medical devices (defibrillators and ultrasound machines), building automation systems, IT (storage systems) and critical systems (avionics navigation, railway infrastructure).
The NUCLEUS:13 vulnerabilities
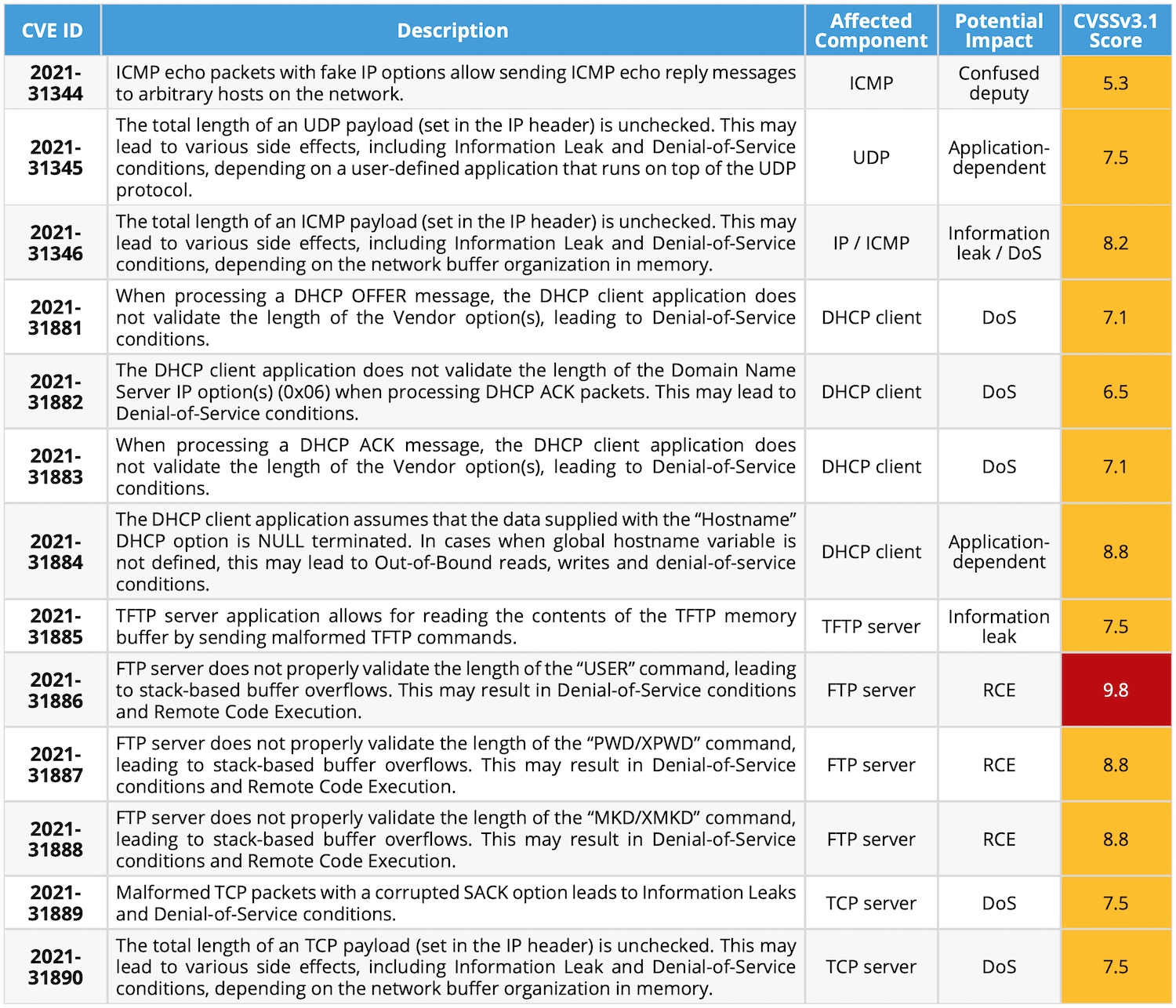
The thirteen vulnerabilities discovered by the researchers in the Nucleus NET TCP/IP stack run the impact gamut from information leak and DoS to remote code execution. Most affect the stack’s FTP/TFTP server and DHCP client.
The most critical of the unearthed flaws is CVE-2021-31886, which stems from the FTP server not properly validating the length of the “USER” command, which may exploited to trigger stack-based buffer overflows and allow attackers to perform controlled writes into the memory of the affected device, hijacking the execution flow and executing attackers’ code. What’s more, prior authentication to the device is not needed for a successful exploitation, the researchers noted.
They demonstrated how the vulnerability could be exploited to, for example, disrupt the functioning of a hospital’s building automation systems (and impact patient care), or the normal functioning of an automated train system (and create the potential for major collisions):
More technical information about the vulnerabilities and possible attacks are included in this technical report.
Mitigating the risk of exploitation
A Shodan search has revealed 1,169 devices running the Nucleus FTP and 1,090 ones running Nucleus RTOS (though they might not all be vulnerable). Queries to the Forescout Device Cloud have revealed close to 5,500 devices from 16 vendors in place at 127 customers.
“Thirteen of these customers had more than 100 vulnerable devices, with healthcare being the most impacted sector,” the researchers noted
As mentioned before, Siemens has already released official patches, and device vendors using this software should provide their own updates to customers.
If specific updates are not yet available, Forescout has recommended several risk mitigation steps.
ICS-CERT has also published an advisory that lists affected products and mitigations.