Regula: Open source policy engine for IaC security
Fugue announced Regula 1.0, an open source policy engine for infrastructure as code (IaC) security. Available at GitHub, the tool includes support for common IaC tools such as Terraform and AWS CloudFormation, prebuilt libraries with hundreds of policies that validate AWS, Microsoft Azure, and Google Cloud resources, and new developer tooling to support custom rules development and testing with Open Policy Agent.
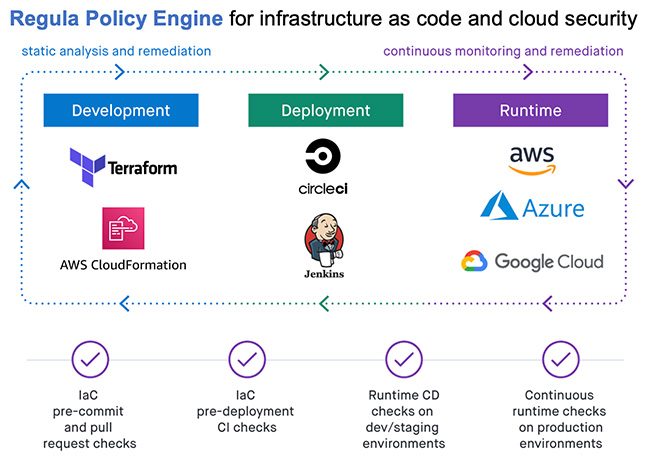
Using Regula
Regula supports a broad set of IaC inputs including Terraform HCL, Terraform plan JSON, AWS CloudFormation, and Serverless Application Model templates.
Extensive rule libraries check for common security and compliance violations and advanced, multi-resource misconfigurations, and can detect when required resources are missing. Regula supports standardized output formats such as JUnit, Test Anything Protocol (TAP), and JSON, allowing it to integrate seamlessly with CI/CD tools and testing frameworks including Jenkins, CircleCI, Travis CI, and Conftest.
Cloud and security engineers can use their Regula policies in the Fugue SaaS platform to check their AWS, Microsoft Azure, and Google Cloud environments, giving them a unified policy engine for securing the entire cloud development lifecycle (CDLC) from IaC through deployment and runtime.
“Infrastructure as code presents cloud teams with the opportunity to shift left on cloud security pre-deployment, and they need better tooling to develop and test policies, integrate them into their CI/CD workflows, and apply those same rules to their cloud runtime environments,” said Josh Stella, CEO of Fugue. “These new Regula capabilities and policies make it easier than ever for cloud teams to secure their IaC and apply policy consistently across the CDLC and across cloud platforms—and avoid the overhead of maintaining and reconciling different policy frameworks.”

Creating custom rules
Regula utilizes the Cloud Native Computing Foundation’s Open Policy Agent framework, with expressive and powerful rules written in the Rego language.
Developers can create their own custom rules to meet organizational requirements, and Regula includes additional tooling for running tests on these rules. Rules can be waived to designate exceptions for specific resources or disabled entirely to fit an organization’s needs.
Regula provides out-of-the-box support for the CIS Foundations Benchmarks; additional Regula policies check for cloud vulnerabilities that compliance frameworks can miss, such as dangerously permissive AWS IAM policies, Lambda function policies allowing global access, EBS volumes with encryption disabled, and untagged cloud resources. View the full set of Regula rules here.
Regula comes as a pre-packaged binary including a CLI, and can be easily installed with Homebrew or deployed with a Docker image that can be found at DockerHub.