What happens to email accounts once credentials are compromised?
Agari researchers entered unique credentials belonging to fake personas into phishing sites posing as widely used enterprise applications, and waited to see what the phishers would do next with the compromised accounts.
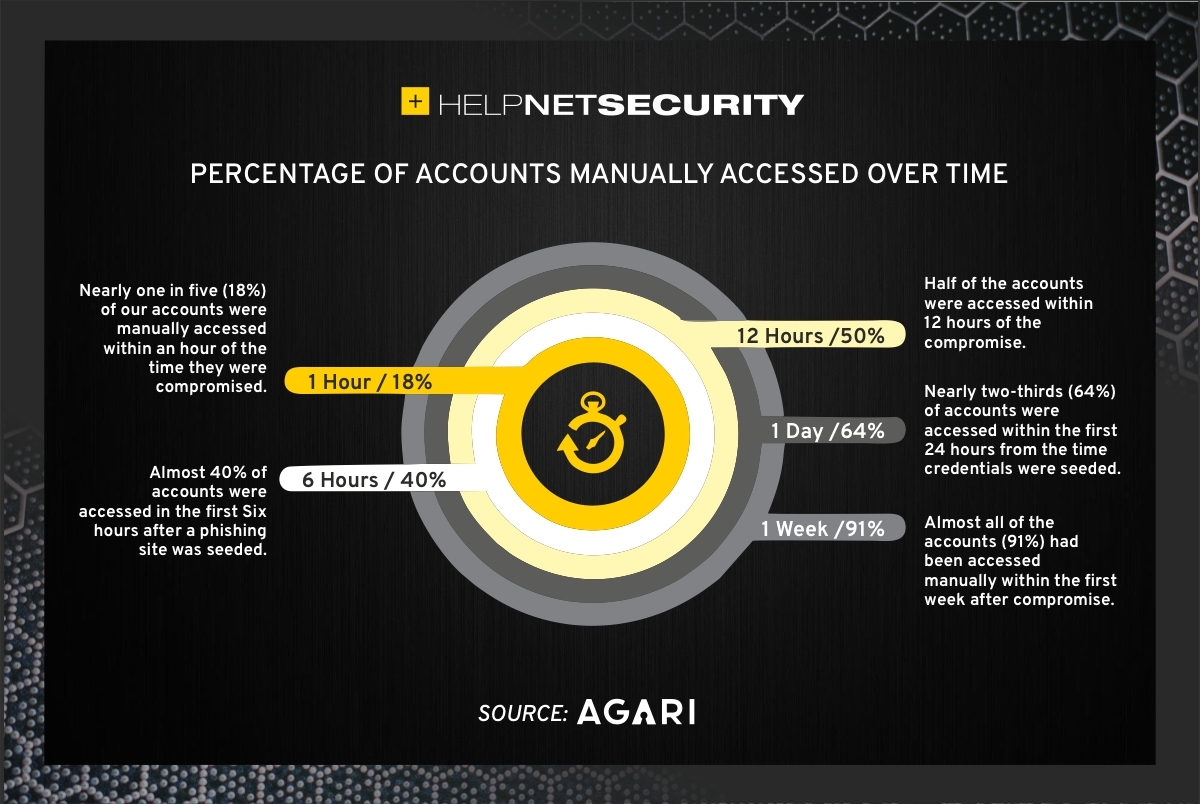
They found that 23% of all accounts were accessed almost immediately (likely in an automated manner, to confirm that the credentials work), 50% of the accounts were accessed manually withing 12 hours after compromise, and that 91% of the compromised accounts were accessed manually within the first week.
How are the compromised accounts used?
The phishing pages into which the researchers seeded the uniqe credentials impersonated Microsoft OneDrive, Office 365, SharePoint, Adobe Document Cloud, or just (generically) Microsoft.
After six months, they detected activity in nearly 40% of their “compromised” accounts.
“Although a majority of the compromised accounts (64%) were only accessed one time, a number of the accounts were accessed repeatedly over an extended period of time. In fact, one account was accessed 94 times over a four-and-a-half month period, a great example of the persistent and continuous access cybercriminals maintain on compromised email accounts,” they noted.
Attackers use hacked enterprise mailboxes to pinpoint employees who have access to a company’s financial information / payment system. They often set up email forwarding or redirect rules to have immediate insight into incoming and outgoing emails.
Some of the attackers pivot from email to other Office 365 applications, the researchers noted, and use those to trawl for valuable documents or even to upload files (fake invoices and similar) that will be used for subsequent phishing attacks or fraud attempts.
But, mostly, the attackers used the hijacked email accounts to send out more phishing emails, sometimes targeting specific industries and sometimes a wide variety of them, and to set up additional business email compromise (BEC) infrastructure (e.g., to register for a variety services that will allow them to perform reconnaissance and lead generation, deliver emails, host malicious pages, or create malicious documents).
“By tricking people into giving up their credentials, threat actors can use legitimate accounts to run their malicious schemes — a dream come true from their perspective,” the researchers noted.
And compromised accounts lead to phishing emails and to more compromised accounts and more phishing – and so on and so forth, in a neverending circle that should be stopped.