New Google tool reveals dependencies for open source projects
Google has been working on a new, experimental tool to help developers discover the dependencies of the open source packages/libraries they use and known security vulnerabilities they are currently sporting.
Open Source Insights
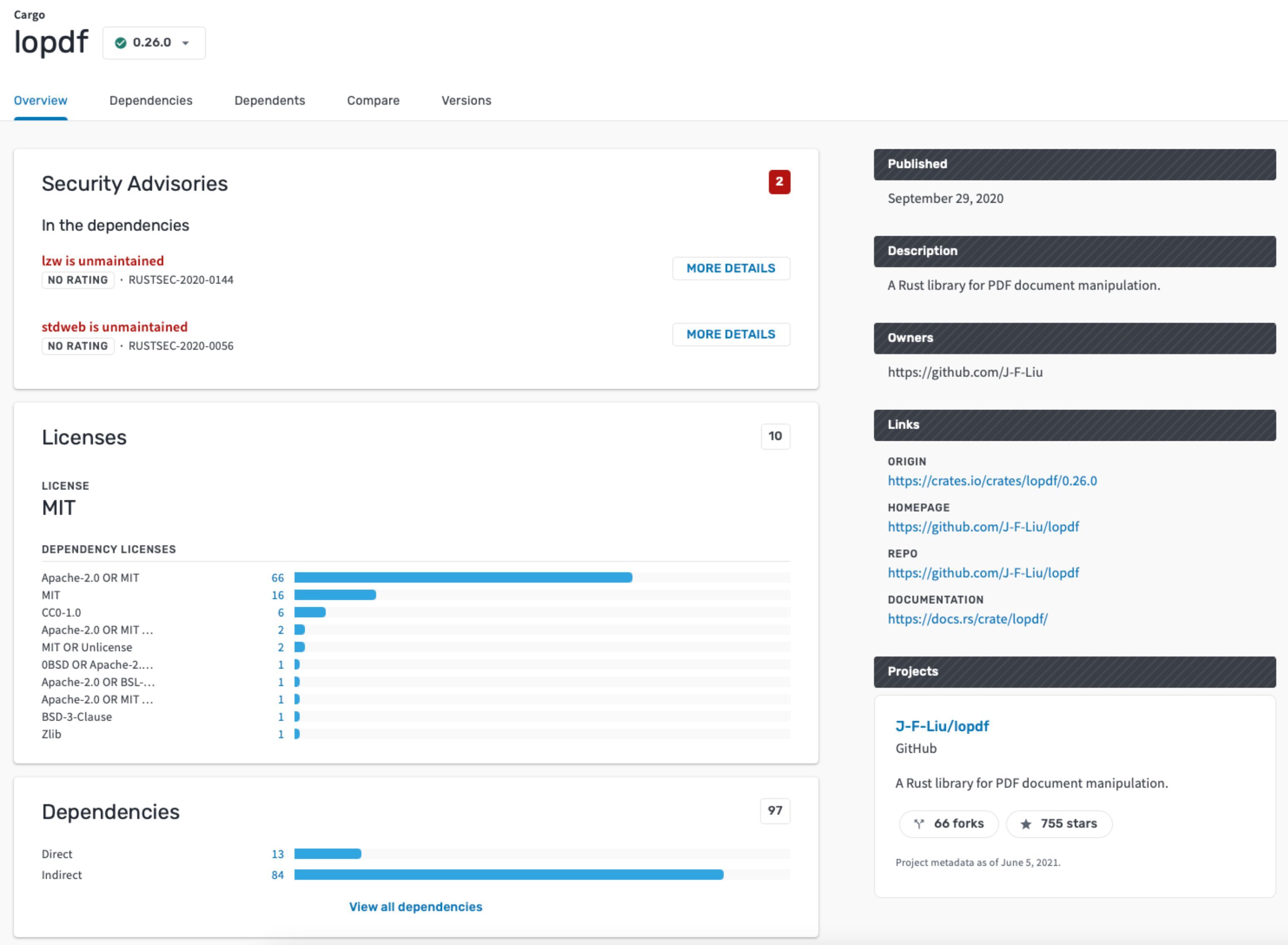
Open Source Insights is a Google Cloud Platform-hosted tool that’s accessible via a website into which users can enter the name of specific open source packages and get an overview of how they are put together.
It shows:
- Information about the packade (description, ownership, links)
- Dependencies (components the package depends on)
- Dependents (packages that depend on it)
- Security advisories (known vulnerabilities in the package and dependencies, unmanaged dependencies, etc.)
- License information
“Among other features, it provides interactive tools to visualize and analyze full, transitive dependency graphs. It also has a comparison tool to highlight how different versions of a package might affect your dependencies, perhaps by changing their own dependencies, adding licensing requirements, or fixing security problems,” the Open Source Insights Team explained.
The tool currently shows information about 50,000 (Rust) Cargo packages (crates), 0.6 million Go modules, 420,000 Maven (Java) and 3.6 million npm packages (Node.js). and Google is working on addind additional packaging systems.
“The project scans all the available packages it can discover, either by reading the package home site for a system like npm, or by scanning GitHub and other repository hosting sites,” they explained.
“At the moment, Insights can only analyze systems, like these, with a known packaging model, since it needs the packaging information to construct the dependency graph. This means that, for now at least, there is no data for C or C++, which do not have a clear packaging model.”
Improving the security of the open source supply chain
As enterprises’ use of open-source software increases and the risks posed by unmanaged open source (including security vulnerabilities, outdated or abandoned components, and license compliance issues) are pervasive, keeping an eye on the many and frequent changes in packages one’s software solutions depend on is a must.
Developers can used vulnerability scanners and dependency audits to identify vulnerabilities, but Open Source Insights offers a bigger picture into the security of your software supply-chain.
“Insights is not an attempt to replace the standard tool set, but rather to augment it with a fresh, integrated view of the whole ecosystem for each packaging model,” Google explained.
“A key difference is that the Insights data is derived from first principles, looking at the software and its packaging definition. The result may be substantially different or more complete than just the declared dependencies of, for instance, a packaging ‘lock’ file. Moreover, the data presented by Insights is re-evaluated regularly, to keep it up to date, which is important in the fast-moving world of open source development.”
Insights tracks various public vulnerability databases to flag known security issues.
The data for commonly used packages is usually fresh and up to date, Google says, but notes that the data for inactive and obsolete packages can be staler.