Exploiting common URL redirection methods to create effective phishing attacks
“Simple” can often be harder than “complex.” When thinking about the trickiest phishing campaigns and their components, URL redirection does not immediately come to mind as the part causing the trouble. However, URL forwarding is one method that is often abused by cybercriminals to create multi-layered phishing attacks. Why? The short answer is in three E’s: easy, evasive, and elusive (to the eye).

URL redirection for malicious purposes
URL redirection is the process of forwarding web users from the originally requested URL to a completely different one. Internet users encounter URL redirects every day, sometimes without noticing it: by clicking on a shortened link to go and read the news, being forwarded from one site to another to buy or pay for an advertised product, etc. URL redirection is so common and has become a part of our daily life online that phishers do not mind exploiting it for their own purposes.
Let’s take a look at examples of three phishing attacks, all with URL redirection playing an integral role:
#1. Encoded, JavaScripted HTML attachment with a delayed phishing redirect inside
This type of attack is not very common, since it includes a large number of components:
- An email with an attachment
- The attachment is a HTML file and JavaScripted
- The URL-encoded phishing redirect in the HTML file exploits the set-timeout method
- The phishing landing page
Imagine receiving a strange email from your corporate IT admin urging you to update something. The email is blank, seemingly sent internally (the sender is spoofed), and contains an “UPDATE.htm” attachment.
When checking the file’s page source code, we can see an encoded script that, once decoded, shows the phishing URL of the web page the recipient would be redirected to after milliseconds of delay (setTimeout method).
The setTimeout() method is used to execute a function only once after a specified number of milliseconds. For example, if this file is opened in a browser, the setTimeout method executes the redirect and forwards the victim to a landing Office365-themed phishing page after 5 milliseconds.
#2. Phishing emails distributed by exploiting Adobe open redirects
The second example also uses a corporate IT admin as cover, but in this case, it is clear that the phishing email is sent from a compromised Japanese mailbox tamariya@tamariya.co.jp that is not associated with the targeted organization or with Microsoft Office 365. The recipients are told that their Office 365 password expires on that day, are told they have to change it or continue to use the current password and are pushed towards an easy choice: clicking on the “Keep Current Password”:

Once they do it, the targets will land on a fake Office 365 login page hosted on the r-im[.]xyz domain, after having been redirected through the Adobe hosting URL.
Abusing Adobe’s open redirect services (t-info.mail.adobe.com) adds legitimacy to the URL, as well as increases the chances for the email to evade detection. These are the main reasons the open redirects of highly trusted companies (Adobe, Google, Samsung) are very popular among phishers.
#3. Shortened URLs hiding the phishing login pages
URL shortening services – such as bit.ly, cutt.ly, t.co, and others – are being actively used by the attackers to mask URLs and to direct targets to a malicious page.
A recently observed attack used cutt.ly to conceal a phishy Netflix login page. What we see below is an email, purportedly sent from Netflix Support, asking the mail recipient to “restart the membership”:
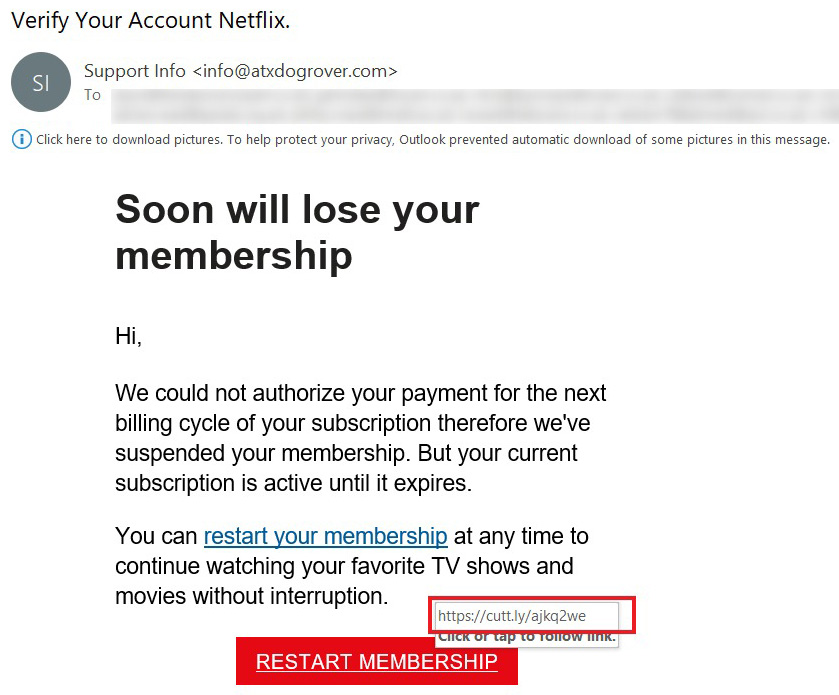
The “Restart Membership” button opens a spoofed Netflix login page, whose URL (https://www.propertyoptionsdevelopments[.]com/netflx20/) has been shortened via cut.ly (https://cutt[.]ly/ajKQ2We). The email was sent from
In conclusion: do not underestimate URL redirection. Be extremely vigilant before opening a link from an unsolicited email, especially when you are not 100% sure where this link will lead you.