Ermetic’s platform provides full stack visibility and control over multi-cloud infrastructure entitlements
Ermetic announced a platform that provides full stack visibility and control over multi-cloud infrastructure entitlements.
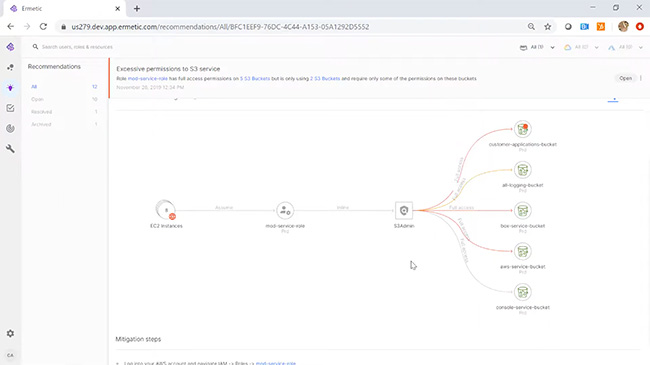
By analyzing identity and access management (IAM) policies as well as the configuration of network, storage and secrets assets, Ermetic eliminates attack surface blind spots and enables organizations to enforce least privilege across their entire cloud infrastructure.
“One of the biggest risks in public cloud security is access abuse, specifically excessive permissions and compromised identities having access to data and resources. The challenge is that enforcing least privilege is much more difficult in the public cloud than on-premises,” said Garrett Bekker, Principal Security Analyst at 451 Research, a part of S&P Global Market Intelligence.
“Many customers are looking to add additional security controls and services themselves, and there’s increased interest in addressing user roles and permissions.”
Full stack visibility of risks
To help security and cloud operations teams reduce their attack surface, Ermetic combines a holistic view of both network access and IAM policy entitlements to comprehensively assess risks.
By monitoring and visualizing both network configurations and identity access policies Ermetic provides the context needed to correctly assess the risk of over privileged and risky entitlements.
For example, a machine with elevated privileges that is exposed to the internet would pose a greater security risk than one with a similar IAM configuration without internet access. This unified visibility is unique to Ermetic and is essential for accurately assessing the “effective access” assigned to a machine or data resource.
“While it’s virtually impossible to determine entitlement risks for users and machines using tools offered by cloud platform providers, third party tools that rely exclusively on identity and access policies without also analyzing network access do not provide a true and accurate view of risks,” said Shai Morag, CEO and Co-Founder of Ermetic.
“Ermetic is the first solution to provide full stack visibility into both identity entitlements and network access configurations, which enables customers to comprehensively assess and govern the risks associated with complex scenarios of users, machines, and resources.”
Shift left with advanced policy automation
To enable organizations to “shift left” and integrate cloud infrastructure entitlements management (CIEM) into their existing workflows and processes, Ermetic has introduced a policy wizard that automates policy administration and risk remediation.
These new capabilities enable Dev, DevOps and Security teams to review and authorize policy changes in a few short steps, and implement them via cloud provider APIs with the push of a button.
Meanwhile, new infrastructure as code (IaC) templates for Terraform (Hashicorp) and Cloud Formation enable policy changes to be made through existing CI/CD pipelines. In addition, a RestAPI enables the sharing of policies and data from Ermetic with enterprise platforms including ticketing systems, SIEM, and more.
Managing third party identities
Governing third party access by contractors, service providers and applications to public cloud environments is both a security and compliance imperative. While it is easy to grant access to third parties, it is difficult to discover and assess their entitlements, as well as re-certify and/or remove them.
To address these risks Ermetic can audit third party users including SaaS applications and APIs, correctly assess their risk, delete inactive accounts, and remove excessive permissions.
Governing federated users
Many organizations provide federated access (SSO) to their cloud resources using external identity providers such as Okta or Azure AD. This creates a blindspot that makes it virtually impossible to manage and control entitlements of federated and external users.
To enable the enforcement of granular access policies on federated identities, Ermetic provides comprehensive visibility into the privileges assigned, needed and in use by each user.