Healthcare network security is slowly improving
Healthcare delivery organizations (HDOs) have been busy increasing their network and systems security in the last year, though there is still much room for improvement, according to Forescout researchers.

This is the good news: the percentage of devices running Windows unsupported operating systems fell from 71% in 2019 to 32% in 2020 and there have been improvements when it comes to timely patching and network segmentation.
The bad news? Some network segmentation issues still crop up and HDOs still use insecure protocols for both medical and non-medical network communications, as well as for external communications.
The findings
Based on two data sources – an analysis of network traffic from five large hospitals and clinics and the Forescout Device Cloud (containing data for some 3.3 million devices in hundreds of healthcare networks) – the researchers found that, between April 2019 and April 2020:
- The percentage of devices running versions of Windows OS that will be supported for more than a year jumped from 29% to 68% and the percentage of devices running Windows OS versions supported via ESU fell from 71% to 32%. Unfortunately, the percentage of devices running Windows OSes like Windows XP and Windows Server 2003 remained constant (though small)
- There was a decided increase in network segmentation
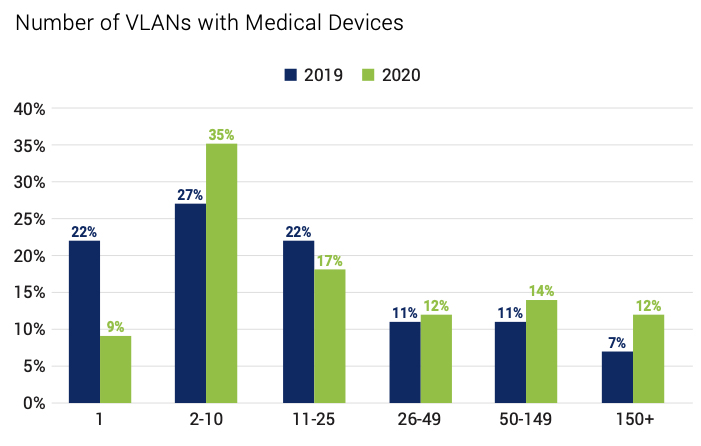
Unfortunately, most network segments (VLANs) still have a mix of healthcare devices and IT devices or healthcare equipment, personal, and OT devices, or mix sensitive and vulnerable devices.
As far as communication protocols are concerned, they found that:
- 4 out of the 5 HDOs were communicating between public and private IP addresses using a medical protocol, HL7, that transports medical information in clear text
- 2 out of the 5 HDOs allowed medical devices to communicate over IT protocols with external servers reachable from outside the HDO’s perimeter
- All HDOs used obsolete versions of communication protocols, internally and externally (e.g., SSLv3, TLSv1.0, and TLSv1.1, SNMP v1 and 2, NTP v1 and 2, Telnet)
- Many of the medical and proprietary protocols used by medical equipment lack encryption and authentication, or don’t enforce its usage (e.g., HL7, DICOM, POCT01, LIS02). OT and IoT devices in use also have a similar problem
That’s all a big deal, because attacks exploiting these security vulnerabilities could do a lot of damage, including stealing patients’ information, altering it, disrupting the normal behavior of medical devices, disrupting the normal functioning of the entire organization (e.g., via a ransomware attack), etc.
Defense strategies for better healthcare network security
The researchers advised HDOs’ cyber defenders to:
- Find a way to “see” all the devices on the network, whether they comply with company policies, and detect malicious network behavior they may exhibit
- Identify and remediate weak and default passwords
- Map the network flow of existing communications to help identify unintended external communications, prevent medical data from being exposed publicly, and to detect the use of insecure protocols
- Improve segmentation of devices (e.g., isolate fragile legacy applications and operating systems, segment groups of devices according to their purpose, etc.)
“Whenever possible, switch to using encrypted versions of protocols and eliminate the usage of insecure, clear-text protocols such as Telnet. When this is not possible, use segmentation for zoning and risk mitigation,” they noted.
They also warned about the danger of over-segmentation.
“Segmentation requires well-defined trust zones based on device identity, risk profiles and compliance requirements for it to be effective in reducing the attack surface and minimizing blast radius. Over-segmentation with poorly defined zones simply increases complexity without tangible security benefits,” they concluded.