A look at the top threats inside malicious emails
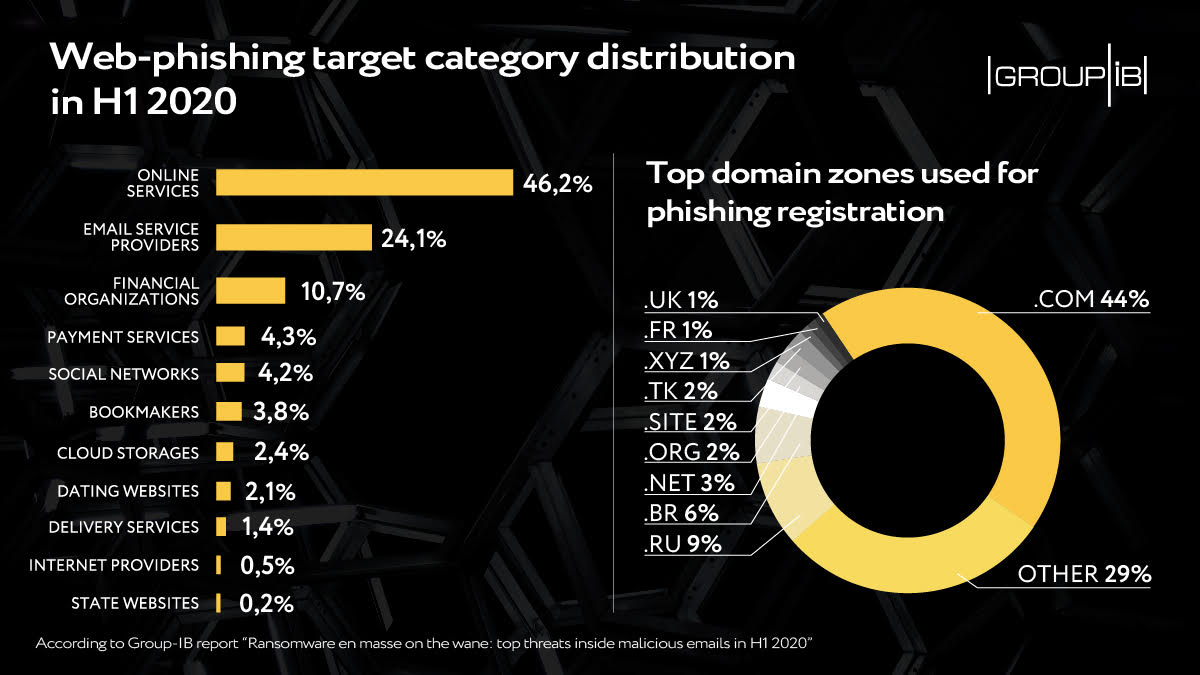
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages, Group-IB reveals.
Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analyzed contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware, and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
Opened email lets spy in
According to the data, in H1 2020, 43 percent of the malicious mails on the radars of Group-IB Threat Detection System had attachments with spyware or links leading to their downloading.
Another 17 percent contained downloaders, while backdoors and banking Trojans came third with a 16- and 15-percent shares, respectively. Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
These findings confirm adversaries’ growing interest in Big Game Hunting. Ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Top-10 tools used in attacks were banking Trojan RTM (30%); spyware LOKI PWS (24%), AgentTesla (10%), Hawkeye (5%), and Azorult (1%); and backdoors Formbook (12%), Nanocore (7%), Adwind (3%), Emotet (1%), and Netwire (1%).
The new instruments detected in the first half of the year included Quasar, a remote access tool based on the open source; spyware Gomorrah that extracts login credentials of users from various applications; and 404 Keylogger, a software for harvesting user data that is distributed under malware-as-a-service model.
Almost 70 percent of malicious files were delivered to the victim’s computer with the help of archives, another 18% percent of malicious files were masked as office documents (with .doc, .xls and .pdf file extensions), while 14% more were disguised as executable files and scripts.
Secure web-phishing
In the first six months of 2020, a total of 9 304 phishing web resources were blocked, which is an increase of 9 percent compared to the previous year. The main trend of the observed period was the two-fold surge in the number of resources using safe SSL/TLS connection – their amount grew from 33 percent to 69 percent in just half a year.
This is explained by the cybercriminals’ desire to retain their victim pool – the majority of web browsers label websites without SSL/TLS connection as a priori dangerous, which has a negative impact on the effectiveness of phishing campaigns.
Experts predict that the share of web-phishing with insecure connection will continue to decrease, while websites that do not support SSL/TLS will become an exception.
Pandemic chronicle
Just as it was the case in the second half of 2019, in the first half of this year, online services like ecommerce websites turned out to be the main target of web-phishers. In the light of global pandemic and the businesses’ dive into online world, the share of this phishing category increased to remarkable 46 percent.
The attractiveness of online services is explained by the fact that by stealing user login credentials, threat actors also gain access to the data of bank cards linked to user accounts.
Online services are followed by email service providers (24%), whose share, after a decline in 2019, resumed growth in 2020, and financial organizations (11%). Main web-phishing target categories also included payment services, cloud storages, social networks, and dating websites.
The leadership in terms of the number of phishing resources registered has persistently been held by .com domain zone – it accounts for nearly a half (44%) of detected phishing resources in the review period. Other domain zones popular among the phishers included .ru (9%), .br (6%), .net (3%) and .org (2%).
“The beginning of this year was marked by changes in the top of urgent threats that are hiding in malicious emails,” comments CERT-GIB deputy head Yaroslav Kargalev.
“Ransomware operators have focused on targeted attacks, choosing large victims with a higher payment capacity. The precise elaboration of these separate attacks affected the ransomware share in the top threats distributed via email en masse.
“Their place was taken by backdoors and spyware, with the help of which threat actors first steal sensitive information and then blackmail the victim, demanding a ransom, and, in case the demand is refused, releasing the info publicly.
“The ransomware operators’ desire to make a good score is likely to result in the increase of the number of targeted attacks. As email phishing remains the main channel of their distribution, the urgency of securing mail communication is more relevant than ever.”